Blockchain technology has dramatically evolved since its origin with Bitcoin in 2009, transforming from a mere cryptocurrency ledger into a broad-based platform for decentralized applications. Its foundational attributes — immutability, transparency, and decentralization — have established blockchain as a robust framework for secure data transactions across various sectors, eliminating the need for traditional intermediaries.
Despite these advances, the concerns around data privacy persist. Even though blockchain ensures secure data transmission via encryption, the requisite decryption for processing opens up potential security loopholes. This vulnerability is particularly acute in areas where data confidentiality and integrity are paramount, such as in decentralized applications (dApps) and financial systems operating within the Web3 framework.
To mitigate these risks, advanced cryptographic methods like Fully Homomorphic Encryption (FHE) and Zero Knowledge Proofs (ZKPs) have gained prominence. These technologies offer revolutionary ways to compute on and verify data confidentiality without revealing the underlying sensitive information.
In this article, we delve into the significance of FHE and ZKP in enhancing blockchain application privacy, highlighting their potential to shape the future of data privacy in blockchain technology.
Introduction
FHE and ZKP trace their origins back several decades. Over time, both FHE and ZKP have evolved significantly, remaining crucial to enhancing data privacy.
Fully Homomorphic Encryption (FHE)
FHE is a sophisticated encryption method that allows functions to be performed directly on encrypted data, preserving its confidentiality throughout the process. Essentially, FHE keeps data encrypted during both storage and computation, treating encryption like a secure “black box” where only the owner of the secret key can reveal the output. Initially conceived in 1978, the concept aimed to modify computer hardware to enable secure processing of encrypted data. However, it wasn’t until 2009, catalyzed by advancements in computing power, that a viable FHE scheme emerged. This breakthrough is largely credited to Craig Gentry, whose innovative work marked a significant milestone in the field.
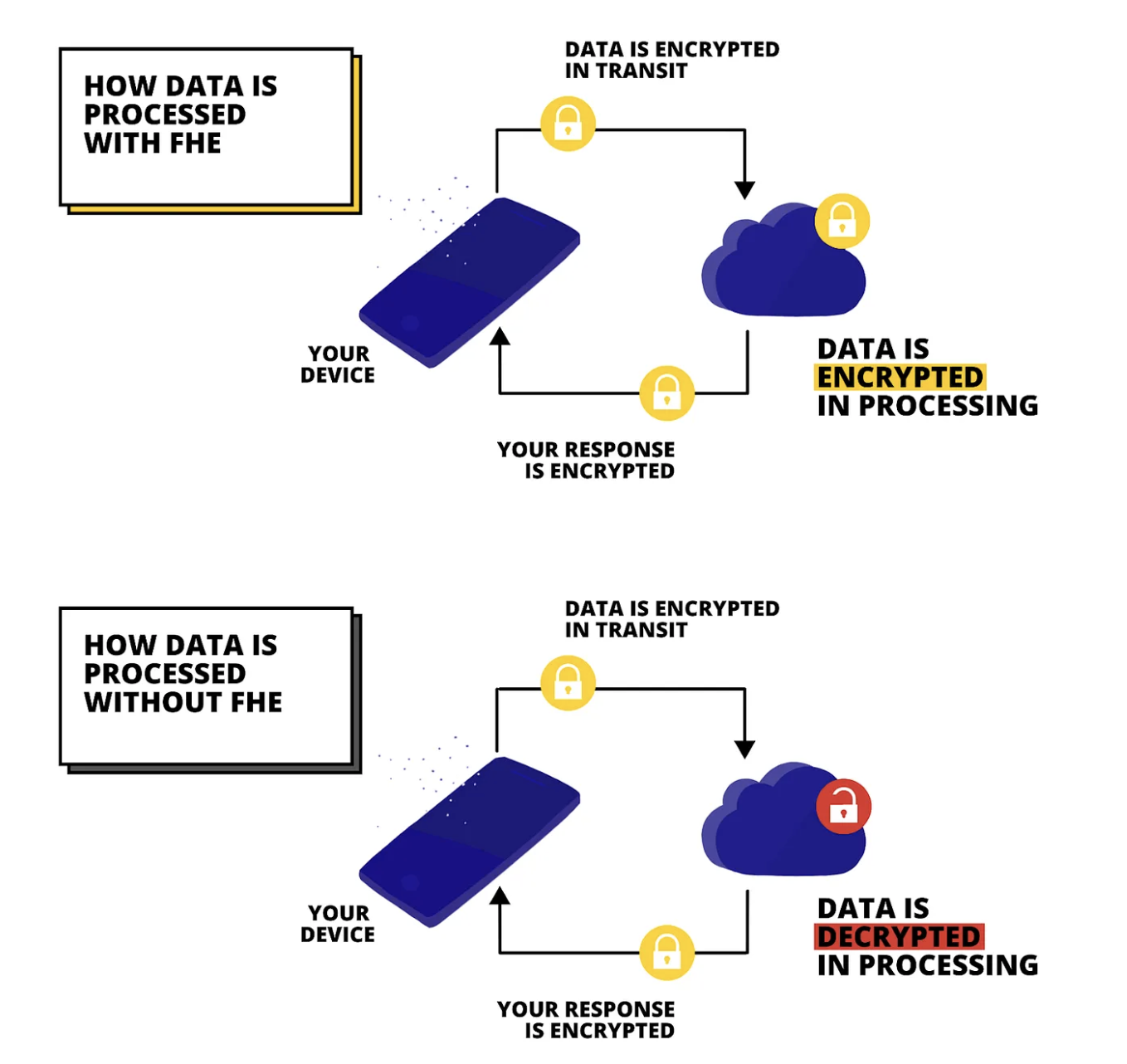
Image via Zama
Key Terms Explained:
- Fully: Indicates the ability to perform a variety of operations, such as addition and multiplication, on encrypted data.
- Homomorphic: Refers to the capability of performing computations directly on encrypted data without decrypting it.
- Encryption: Describes the process of converting information into a secure format to prevent unauthorized access.
Since 2009, notable progress has been made in FHE, one major breakthrough came in 2013, which streamlined the relinearization process and significantly improved FHE’s efficiency. These developments underscore FHE’s capacity to perform a range of arithmetic operations on encrypted data, preserving data security and integrity without exposing it.
Zero Knowledge Proofs (ZKP)
ZKPs were introduced in the seminal 1985 paper “The Knowledge Complexity of Interactive Proof Systems” by Shafi Goldwasser, Silvio Micali, and Charles Rackoff. Originally theoretical, ZKPs underwent a significant evolution in 2012 with the discovery of zk-SNARKs, a type of ZKP that could authenticate virtually any computation while revealing minimal information.
In a typical ZKP, there are two primary roles: the prover and the verifier. The prover aims to confirm a specific claim, and the verifier’s role is to assess the claim’s truth without learning any additional information. This approach allows the prover to disclose only the necessary proof needed to validate the statement, thus preserving data confidentiality and enhancing privacy.
The practical applications of ZKPs have surged with the rise of blockchain technologies and cryptocurrencies. They are now pivotal in facilitating private transactions and enhancing the security of smart contracts. The advent of zk-SNARKs catalyzed the development of solutions like zCash, zkRollups, and zkEVMs, transforming a previously academic pursuit into a vibrant ecosystem filled with real-world applications. This transition highlights the increasing relevance of ZKPs in securing decentralized systems like Ethereum and promoting a robust privacy-centric digital infrastructure.
ZK vs FHE
While FHE and ZKP share some similarities, they diverge significantly in functionality. FHE can compute directly on encrypted data without revealing or accessing the raw data, producing accurate results without exposing the underlying information.
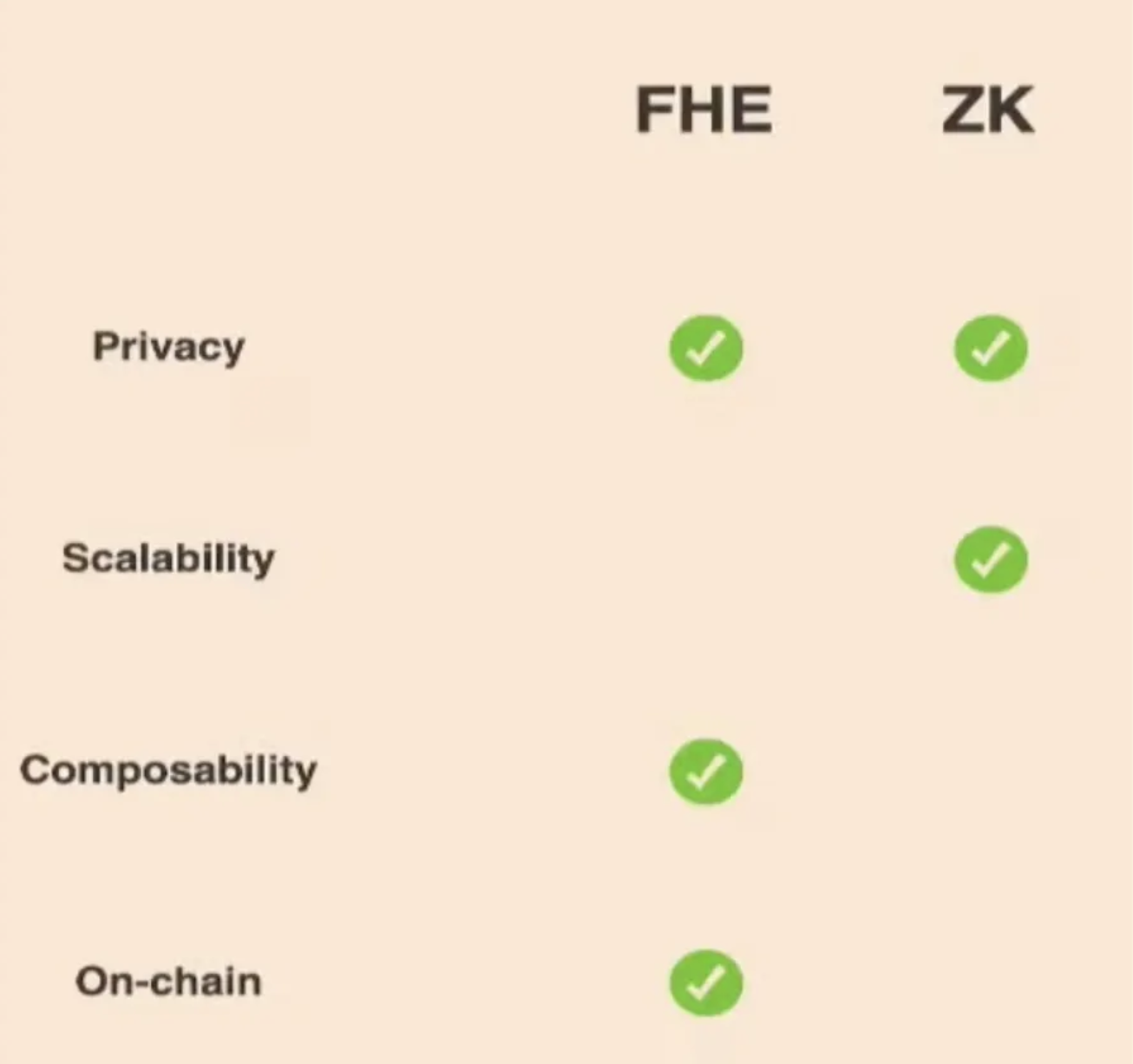
Image via “Morten Dahl — Homomorphic Encryption in the EVM” workshop
Here’s how they differ:
Encryption Computation: ZKP struggles to compute over encrypted data from multiple users, such as private ERC-20 tokens, without compromising security. In contrast, FHE excels in this area, offering greater flexibility and composability across blockchain networks. However, ZKP often requires tailored integrations for each new network or asset.
Scalability: Currently, ZKP is considered more scalable than FHE. However, FHE is expected to improve in scalability as technological advancements continue in the coming years.
Complex Calculations: FHE is well-suited for performing intricate calculations on encrypted data, making it ideal for applications like machine learning, secure MPC, and fully private computations. In comparison, ZKP is typically used for simpler operations, such as proving a specific value without disclosing it.
Universal Applicability: ZKPs excel in particular applications like identity verification, authentication, and scalability. However, FHE can be utilized across a broader spectrum of applications, including secure cloud computing, privacy-preserving AI, and confidential data processing.
This comparison underscores the distinct advantages and constraints of each technology, illustrating their relevance to different scenarios. Both technologies are integral to blockchain applications, but ZKP currently has a more established track record. Despite this, there is potential for FHE to evolve and potentially become the more fitting solution for privacy preservation in the future.
Joint Use of ZKP & FHE
Some applications have intriguingly experimented with combining ZKPs and FHE. Notably, Craig Gentry and his colleagues have explored ways to reduce communication overhead using hybrid fully homomorphic encryption techniques. These innovative techniques have been applied in various blockchain contexts and hold promise for exploration in other fields as well.
Potential applications for ZKPs and FHE include:
1. Secure Cloud Computing: FHE encrypts data while ZKPs verify its correctness, enabling secure computations in the cloud without exposing the original data.
2. Electronic Voting: This combination ensures the confidentiality of votes and confirms accurate vote counting.
3. Financial Transactions: In finance, this integration maintains transaction confidentiality while allowing parties to verify transaction correctness without revealing detailed information.
4. Medical Diagnostics: Encrypted medical data can be analyzed by healthcare providers who can confirm diagnoses without accessing sensitive patient information.
The integration of ZKPs and FHE holds promise for enhancing both identity and data security within applications, meriting further exploration and research.
Current FHE projects in blockchain
- Zama — an open-source cryptography company dedicated to developing FHE solutions for blockchain and AI.
- Secret Network — launched in 2020, is a blockchain platform that incorporates privacy-preserving smart contracts.
- Sunscreen — a compiler specifically designed for FHE and ZKPs.
- Fhenix — a confidential Layer 2 blockchain that leverages FHE technology.
- Mind Network — offers a general-purpose restaking rollup solution based on FHE.
- Privasea — a data infrastructure platform that employs FHE technology, facilitating computations on encrypted data.
Conclusion
FHE is rapidly establishing itself as a fundamental component of cybersecurity, especially evident in cloud computing where industry giants like Google and Microsoft are adopting it to process and store client data securely without compromising privacy.
This technology promises to reshape data security across various platforms, heralding a new era of unmatched privacy. Achieving this future will require continued advancements in both FHE and ZKPs. Collaborative efforts across disciplines — cryptographers, software engineers, hardware specialists, and policymakers — are essential to navigate regulatory landscapes and foster wider adoption.
As we edge toward a new era of digital sovereignty, where data privacy and security are seamlessly integrated, staying informed about the latest developments in FHE and ZKPs cannot be overstated. Keeping informed will empower us to navigate this evolving landscape effectively, harnessing these advanced cryptographic tools to their fullest potential.

