background
Recently, we received a request for help from a user who was attacked by a phishing attack. The user discovered abnormal authorization records in their wallet, attempted to revoke the authorization but was unable to do so, and provided the affected wallet address: 9w2e3kpt5XUQXLdGb51nRWZoh4JFs6FL7TdEYsvKq6Wb. Our on-chain analysis revealed that the user's account owner privileges had been transferred to the address GKJBELftW5Rjg24wP88NRaKGsEBtrPLgMiv3DhbJwbzQ. Furthermore, the user had over $3 million worth of assets stolen, and approximately $2 million worth of assets were held in a DeFi protocol but could not be transferred (this $2 million worth of assets has now been successfully recovered with the assistance of the relevant DeFi provider).
(https://solscan.io/tx/524t8LW1PFWd4DLYDgvtKxCX6HmxLFy2Ho9YSGzuo9mX4iiGDhtBTejx7z7bK4C9RocL8hfeuKF1QaYMnK3itMVJ)
The victim attempted to transfer funds from the account to their own address to verify authorization, but all transactions failed. This situation is highly similar to the "malicious multi-signature" attacks that frequently occur in the TRON ecosystem. In other words, this attack is not a traditional "authorization theft," but rather the core permissions (Owner permissions) being replaced by the attacker, rendering the victim powerless to transfer funds, revoke authorization, or manipulate DeFi assets. The funds are "visible," but no longer under their control.
Solana Owner Modification Mechanism
Attackers successfully tricked users into clicking using two counterintuitive scenarios:
1. Normally, when signing a transaction, the wallet simulates the execution result of the transaction. If there is a change in funds, it will be displayed on the interactive interface. However, a carefully crafted transaction by an attacker will not show any change in funds.
2. Traditional Ethereum EOA accounts are owned by private keys, and users are unaware that Solana has the capability to modify account ownership.
Let's analyze what exactly the Solana Owner modification is.
Account ownership
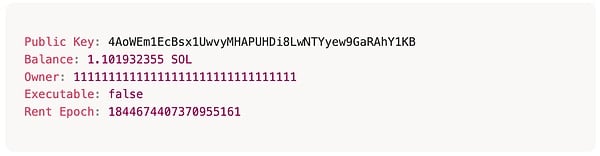
When creating an account in a wallet, the Owner is typically the system account (11111111111111111111111111111111). During transactions, the system verifies that the transaction signature was signed with the corresponding public key. You can view basic account information using the Solana Account command.
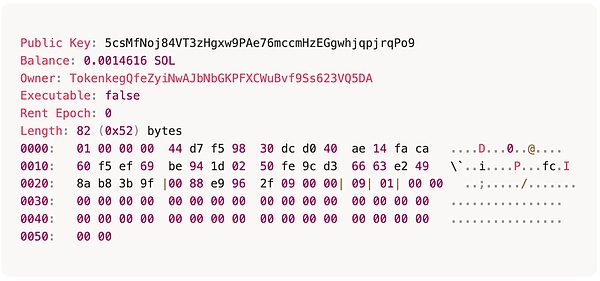
Another type of account is called a PDA account, which is derived from a smart contract and is mainly used to store smart contract data. Its owner is the smart contract from which it is derived. For example, an account used to store token issuance and holding information is a PDA account. When viewing the basic information of an account using Solana Account, you can see that its owner is the token smart contract TokenkegQfeZyiNwAJbNbGKPFXCWuBvf9Ss623VQ5DA.
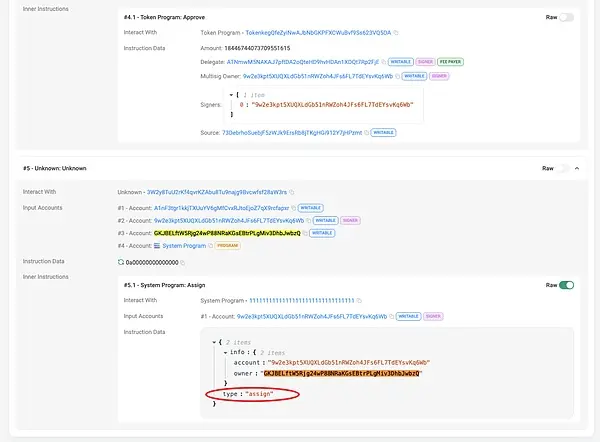
Both types of accounts can change the Owner, but they have different rules and restrictions:
Regular account
The Owner cannot be directly modified externally via commands or scripts, but it can be modified through smart contract calls. The key instructions are as follows:
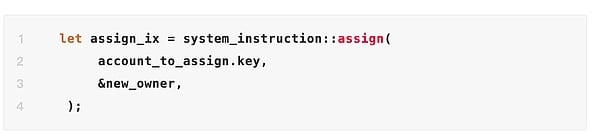
The `assign` command changes the account's Owner from its current value to `new_owner`. After deployment, this command is invoked using the Solana CLI or a client (such as Solana Web3.js). This phishing attack exploited this feature to trick victims into signing transactions containing the `assign` command, thus silently transferring the Owner from the victim's wallet address.
PDA account
In short, the PDA account can modify the Owner, but the account's data must be empty. This is done using the `assign` command. We conducted simple tests on the feedback from modifying the Owner in several scenarios:
1. Newly created PDA accounts can specify any Owner. If the Owner is not the Program that created it, then the Program has no write permissions.
2. When attempting to modify the Owner of a newly created PDA account, the following error occurs: "instruction illegally modified the program id of an account".
3. Before the PDA account is finally assigned data, an attempt is made to write data: instruction modified data of an account it does not own.
Once the owner of an account is changed, the user loses control of the account, and attackers can transfer account assets through CPI calls.
Another common type of ownership change is the ownership of a token account. Essentially, this is ownership controlled by the logic within a smart contract, not by the underlying logic of Solana. However, it is also frequently used in phishing attacks, and users should be wary of this type of phishing attack.
MistTrack Analysis
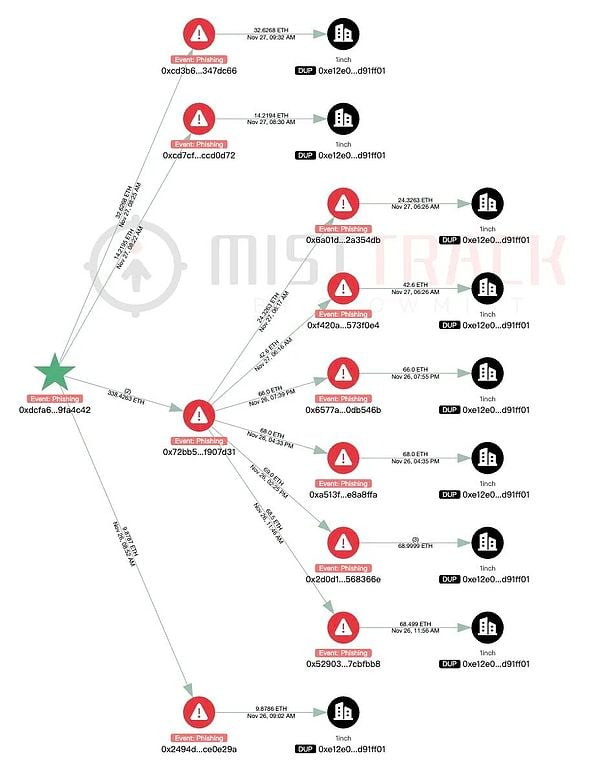
According to the analysis of the victim's address 9w2e3kpt5XUQXLdGb51nRWZoh4JFs6FL7TdEYsvKq6Wb by the on-chain tracing and anti-money laundering tool MistTrack, the fund transfer path in this attack was complex. The attackers mainly diverted assets through two core addresses: BaBcXDg… (flow to 1) and 7pSj1R… (flow to 2).
Flow direction 1: BaBcXDgbPgn85XtEQK7TZV8kZuFpT4iWVAs4QJoyNSmd
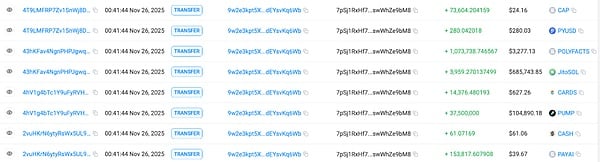
The first main path involved assets worth approximately $2.38 million, characterized by "multi-level diffusion + decentralized deposits through CEXs + multiple address intermediaries." The attackers used this address to exchange various tokens (including PAYAI, CASH, CARD'S, JitoSOL, POLYFACTS, PUMP, PYUSD, and CAP) for SOL. Specifically, PUMP was transferred to 7E4eNkK… before being exchanged for SOL.
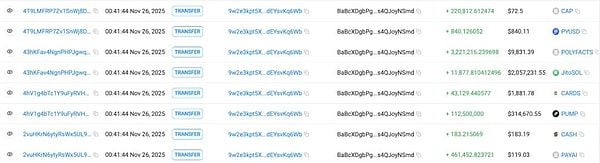
The main destinations of the exchanged SOL are as follows:
1) 717.5 SOL was transferred to YDrMfsB…, some SOL was transferred to the Binance platform, and the remaining funds were dispersed and remained in about 4 transit addresses.
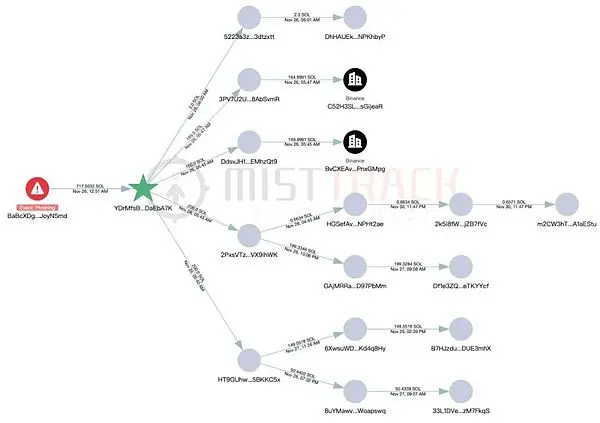
2) 7,556.89 SOL + 2,218 SOL (from PUMP exchange) were uniformly aggregated to 7E4eNkK…, then some SOL were transferred to the Letsexchange platform, 5,050.93 SOL were transferred to FyB2jDJbTdmW…, and the remaining funds were dispersed and remained in about 13 transit addresses.
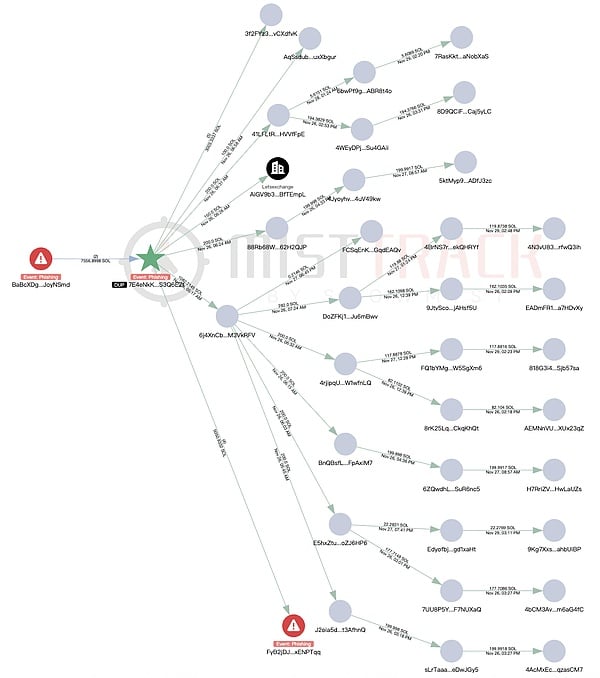
3) 2,161.88 SOL + the aforementioned 5,050.93 SOL were further dispersed in FyB2jD… and transferred to multiple platforms (HTX, Binance, Kucoin, ChangeNOW, Changelly), with some flowing into an unknown address (25nULbv…). The remaining funds were dispersed and remained in approximately 25 transit addresses.
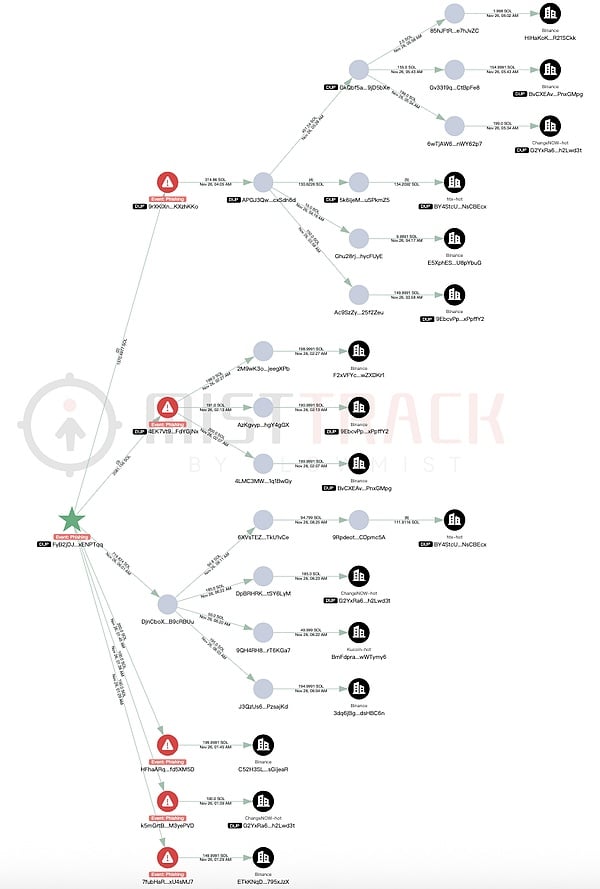
4) 2,053 SOL were transferred to 6qdtH5D…, some SOL were transferred to the Letsexchange platform, and the remaining funds were dispersed and remained in about 15 transit addresses.
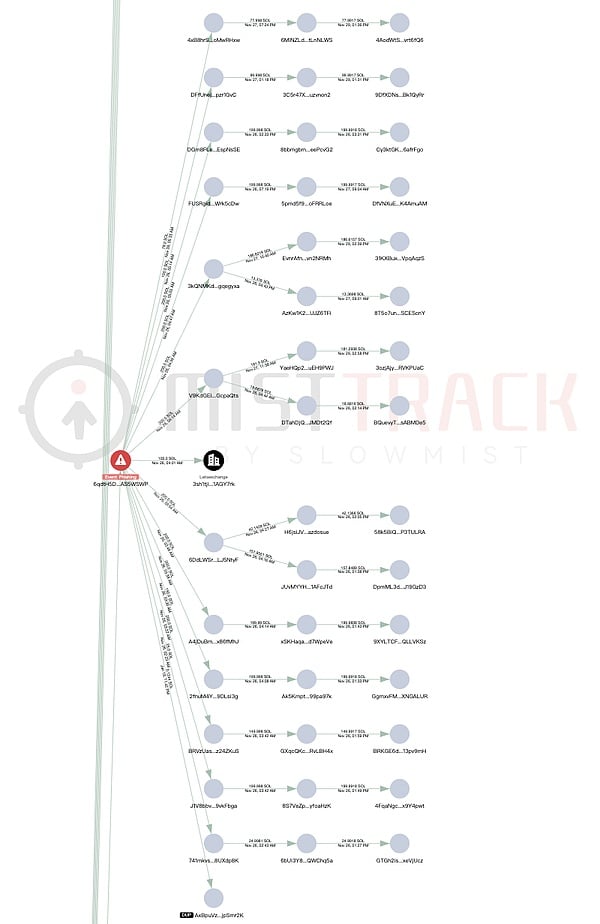
5) 20 SOL is transferred to 5rJdvkp…, then transferred and remains at address 2etvjZH….

6) 2,142 SOL were transferred to 2xFzAda…, 352 SOL were transferred to the Binance platform, 200 SOL were transferred to the Letsexchange platform, and the remaining funds were dispersed and remained in approximately 11 transit addresses.
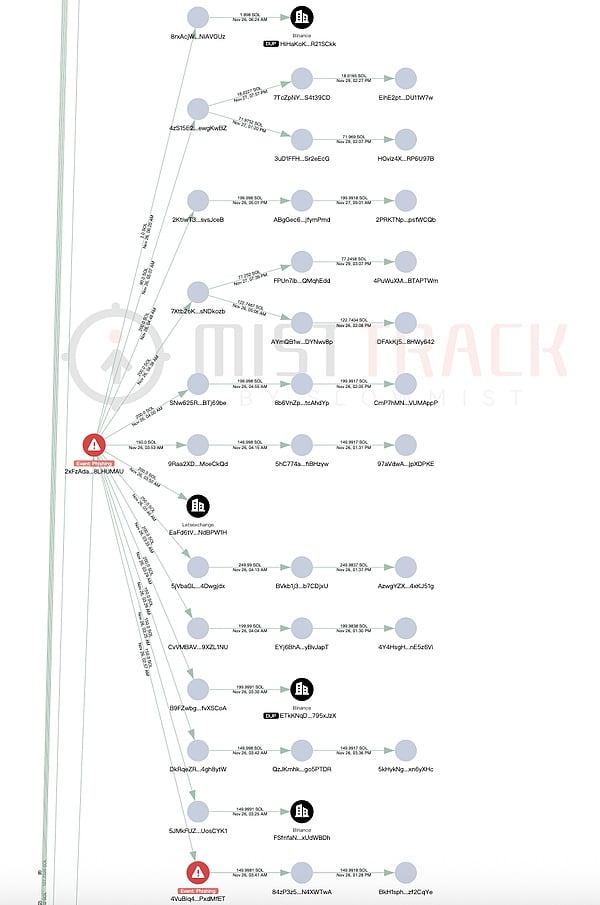
Flow direction 2: 7pSj1RxHf77G3XeisvnNAtbyx5AFjYPcChswWhZe9bM8
The second main path involves assets worth approximately $790,000, with the core characteristic being "cross-chain and multi-chain circular exchange." The attackers also exchanged various received tokens for SOL, with JitoSOL, PUMP, and POLYFACTS accounting for a relatively high proportion.
The main destinations of the exchanged SOL are as follows:
5,742 SOL were transferred to FiywJZ2Z…, which also received 2,772.8 SOL from another phishing event address marked “Phishing” by MistTrack.
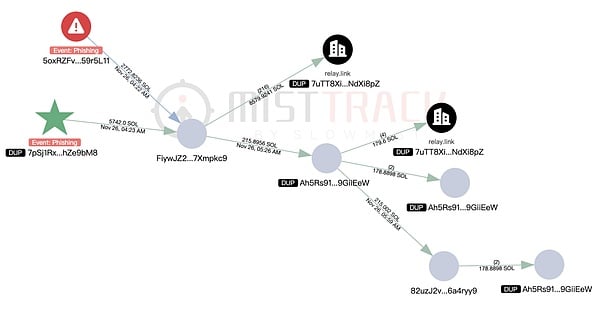
The attackers used Relay.link to exchange 8,579.92 SOL for ETH and cross-chain to the Arbitrum address 0xDCFa6f…, then used 1inch to exchange the funds for SOL and cross-chain to multiple Solana addresses. They then used 1inch repeatedly for cross-chain operations, which will not be elaborated on here.
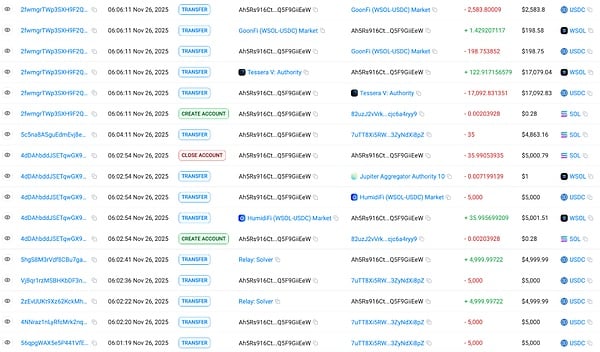
FiywJZ2Z… transferred the remaining 215.89 SOL to Ah5Rs916…, which was then exchanged for 29,875 USDC. The USDC was then exchanged for DAI via Relay.link in increments of 5000, 5000, 5000, 5000, and 19,875.38, and transferred across chains to Base and Ethereum address 0xd2c1c2A…. Two of the 5000 USDC transactions were returned, and the DAI has not yet been transferred out.
DeFi Asset Rescue
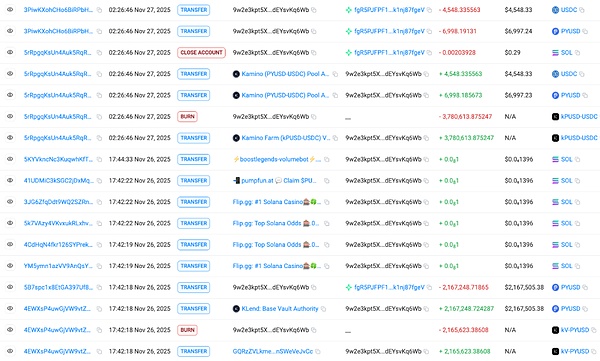
Furthermore, with the assistance of multiple parties, the victim's remaining assets in DeFi were successfully withdrawn and transferred through the address fgR5PJF…, including approximately 2.17 million PYUSD and 4,548 USDC.
This money flow clearly reveals the attacker's behavioral pattern: rapid dispersion, multiple address jumps, multi-platform mixing, cross-chain circulation, and simultaneous CEX deposits and DeFi asset reuse, constructing a multi-level, cross-ecosystem money laundering network that greatly increases the difficulty of tracking. MistTrack has already marked all related addresses.
How can we prevent similar attacks?
For ordinary users, this type of attack is essentially a "phishing attack." Attackers will disguise links in various ways, such as airdrops, rewards, tasks, early test qualifications, or even pretend to be official announcements, making people think it's just a simple operation. In reality, the pop-up signature hides high-risk permissions such as modifying the owner. Once signed, the wallet is basically taken over. Therefore, the most important prevention method is to think carefully before clicking on links and "signatures": Is the source trustworthy? Is this page official? What does this signature actually do? If the content that pops up in the wallet is completely incomprehensible, or if it suddenly contains strange permissions, unfamiliar addresses, or inexplicable requests for authorization, then you must stop immediately and never force yourself to click confirm.
Avoid using wallets containing large amounts of assets for everyday interactions. For tasks, projects, and airdrops, prepare a separate account with a low balance specifically for interaction. Keep your truly important assets in a separate wallet or even a cold wallet. This way, even if you accidentally sign in, you can minimize losses. Additionally, avoid granting unlimited permissions; limit the scope and amount of permissions whenever possible to reduce the space for attackers to abuse the service.
In short, take an extra look, double-check, avoid clicking or signing randomly, and create layers of protection for yourself; store large assets separately, using a secondary account for interaction and the primary account only for safekeeping; stop immediately if you encounter any anomalies, and don't take chances. By doing these things, the risk of being attacked by this type of phishing attack can be significantly reduced. Finally, I highly recommend reading "The Blockchain Dark Forest Self-Help Handbook" (https://darkhandbook.io/).

