
Researchers from cybersecurity media Cybernews disclosed on June 19 that they had discovered one of the largest data leaks in recorded history, involving 16 billion login credentials from numerous online service providers including Apple, Google, and Meta, with the largest number of records in a single database reaching 3.5 billion.
Vilius Petkauskas of Cybernews said that researchers have been investigating the data breach since the beginning of the year and have found "30 exposed datasets, each containing tens of millions to more than 3.5 billion records." Petkauskas confirmed that the total number of records exposed has reached 16 billion.
The Cybernews team believes the massive data set stems from a series of information-stealing malware attacks that harvested credentials from a multitude of online platforms, including social media sites, corporate networks, VPN services, developer portals, and government systems.
The datasets vary in size and name, with some bearing generic labels like “logins” or “credentials,” while others indicate their likely origins, such as one dataset referencing the Russian Federation containing more than 455 million records and another linked to Telegram containing more than 60 million records.
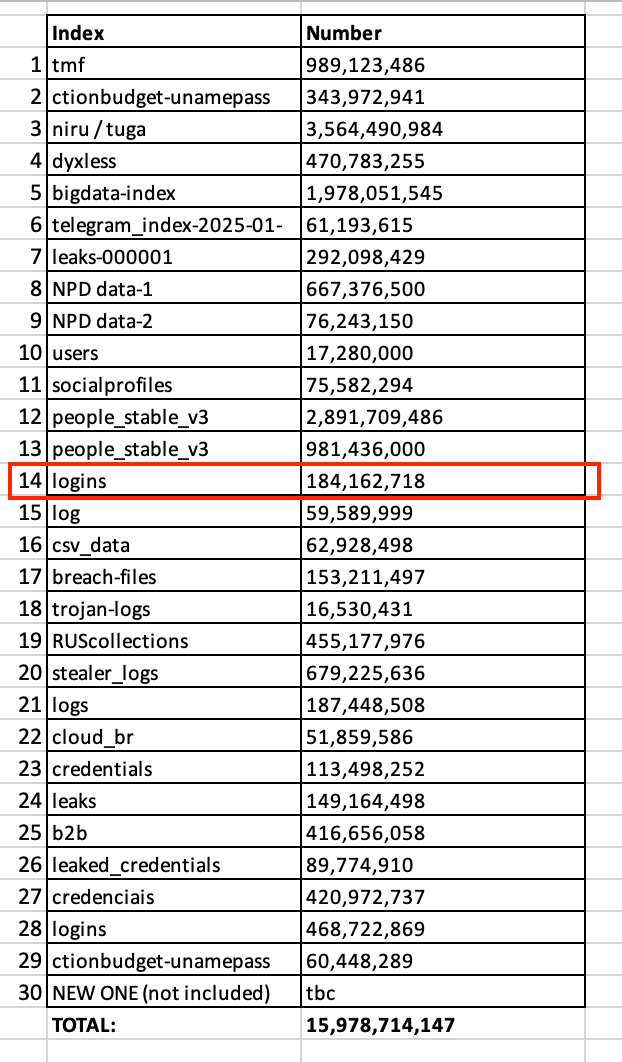
A "mysterious database" containing 184 million records. Courtesy of Bob Diachenko.
How to avoid data security?
Following the incident, Google recommended that billions of users replace old passwords with more secure keys.
Paolo Ardoino, CEO of stablecoin issuer Tether, said in his latest social media post that cloud services have let him down again, "16 billion passwords have just been leaked, it's time to abandon cloud storage." He also announced the upcoming launch of a locally-run password manager - PearPass - a password manager described as "completely local, open source" , where all data (including passwords and encryption keys) will be stored only on the user's device, without reliance on cloud storage.
Looking back at historical data leaks, we can see that data security has always been threatened. According to the 2024 data security incidents collected by Ernst & Young, there were dozens of global data security incidents in 2024 alone from electric vehicles, composite material manufacturers, non-profit organizations, medical care, education, communications and other fields.
For example, in December 2024, Volkswagen software company Cariad disclosed data collected from about 800,000 electric vehicles. This information may be related to the driver's name and reveal the precise location of the vehicle. Because terabytes of Volkswagen customer details in Amazon's cloud storage have been unprotected for months, anyone with a little technical knowledge can track the driver's movements or collect personal information.
On December 16, 2024, medical software service company Phreesia notified more than 910,000 users that its subsidiary ConnectOnCall had suffered a data breach. It is believed that the leaked information includes the content of patients' communications with medical service providers, such as name, phone number, date of birth, medical record number, health status, treatment and prescription information, and some also involve social security numbers.
Good news from decentralized cloud services
All data, including passwords and encryption keys, is stored on the user's device, with no reliance on cloud storage.
Paolo Ardoino, CEO of Tether, tried to ensure data security by not storing data in the cloud, which PowerBeats believes is questionable. There are two difficulties that need to be solved when data is not stored in the cloud. First, the storage capacity and operating performance of hardware devices (mobile phones/computers) need to be further improved . When the storage capacity problem is solved, whether the hardware devices that store a large amount of data can operate smoothly is a topic that needs further research. With the interaction of massive data such as AI and the metaverse, the difficulty will be further escalated. Second, in the era of AI and the metaverse, cloud services are an indispensable part of immersive virtual interactive experiences and scenarios such as autonomous driving that require high edge computing - the processing of massive data needs to rely on the cloud .
At this time, the market needs a service that is both cloud-based and can ensure data security. PowerBeats believes that decentralized cloud services (including decentralized cloud storage and decentralized cloud computing) provide such a solution.
Decentralized cloud services are based on blockchain technology and privacy computing (such as zero-knowledge proof), providing new solutions for data security and are in line with the future development of Internet technology .
Decentralized Storage
Traditional cloud storage relies on centralized servers, which makes them a target for hacker attacks. Decentralized cloud storage stores data on multiple nodes of the network, reducing the risk of single point failure. At the same time, data is usually encrypted and stored in pieces, so even if the data of some nodes is compromised, attackers cannot obtain complete and readable data.
Privacy computing technology
Using privacy computing technologies such as zero-knowledge proof, the authenticity of data can be verified or calculations can be performed without exposing the data itself. This is particularly important for protecting sensitive information, such as in financial transactions, personal identity verification, etc., to ensure the security and privacy of user data.
Smart Contracts
Blockchain-based smart contracts can automatically execute predefined rules and conditions without the intervention of a third party, thereby improving transparency and efficiency while reducing the possibility of human error and fraud, and further enhancing data security .
With the development of the Metaverse, the demand for efficient and secure data processing and storage is growing . Decentralized cloud computing can provide a distributed infrastructure that supports real-time data processing and large-scale concurrent access to meet the high requirements of users in the Metaverse. For application scenarios that require low-latency responses, such as autonomous driving, decentralized cloud computing can process data through nodes close to the data source, reduce transmission delays, and increase processing speed, while also ensuring data security and privacy.
The core lies in data sovereignty - users own their own data, including who can access it and how it is used. This approach promotes a more fair and transparent digital environment, in line with the trend of emphasizing user privacy and data sovereignty in the Web3 era .
Conclusion
To sum up, decentralized cloud services, by combining emerging technologies such as Web3.0 technology, not only ensure data security, but also provide a feasible path to meet the challenges of future Internet technology development.
At present, decentralized cloud services have quietly laid out in the fields of storage and computing, and have deeply integrated other cutting-edge technologies such as intelligent computing, edge computing, DID (decentralized identity), DAO (decentralized autonomous organization), cryptocurrency, etc. For example, the domestic decentralized cloud computing project PowerVerse has cooperated with the three major operators of China Mobile, China Unicom, and China Telecom to initially solve the gaming scenario where users can use cloud computing power uniformly without changing operators.
The shocking data security leaks we have seen so far are caused by the flawed structure of centralized cloud services. With the development of decentralized cloud services, data security will be effectively guaranteed.
refer to:
https://www.anyong.net/shijian
Disclaimer: This article is an original article from PowerBeats and does not constitute investment and application advice. You are welcome to share this article with more friends. When media, brands and related platforms reprint it, they must indicate that it is from PowerBeats.

