Hash (SHA1):e27d3a91876168f2bee3c65d719eba4d48544131 No.: Lianyuan Security Knowledge No.148
In 2024, the global cryptocurrency ecosystem is still developing amid security risks. This year, hacker attacks and phishing scams increased significantly, with phishing losses surging 140.66% year-on-year, with total losses reaching $2.513 billion . Although the industry has strengthened its protection of blockchain security, fund thefts are still common, reflecting the urgency of strengthening technology and defense systems. [The following data is from Chainalysis and Beosin]
Overview of hacker attack trends in 2024
- The amount of theft hits a new high
- The amount of cryptocurrency stolen in 2024 reached US$2.513 billion, an increase of 21.07% year-on-year, making it the fifth year with a total amount of stolen funds exceeding US$1 billion.
- Hacker attacks: $1.792 billion (131 incidents)
- Rug Pull: $148 million (68 incidents)
- Phishing scams: $574 million
- The number of attacks increased from 282 in 2023 to 303, indicating that hacker activity continues to be high.
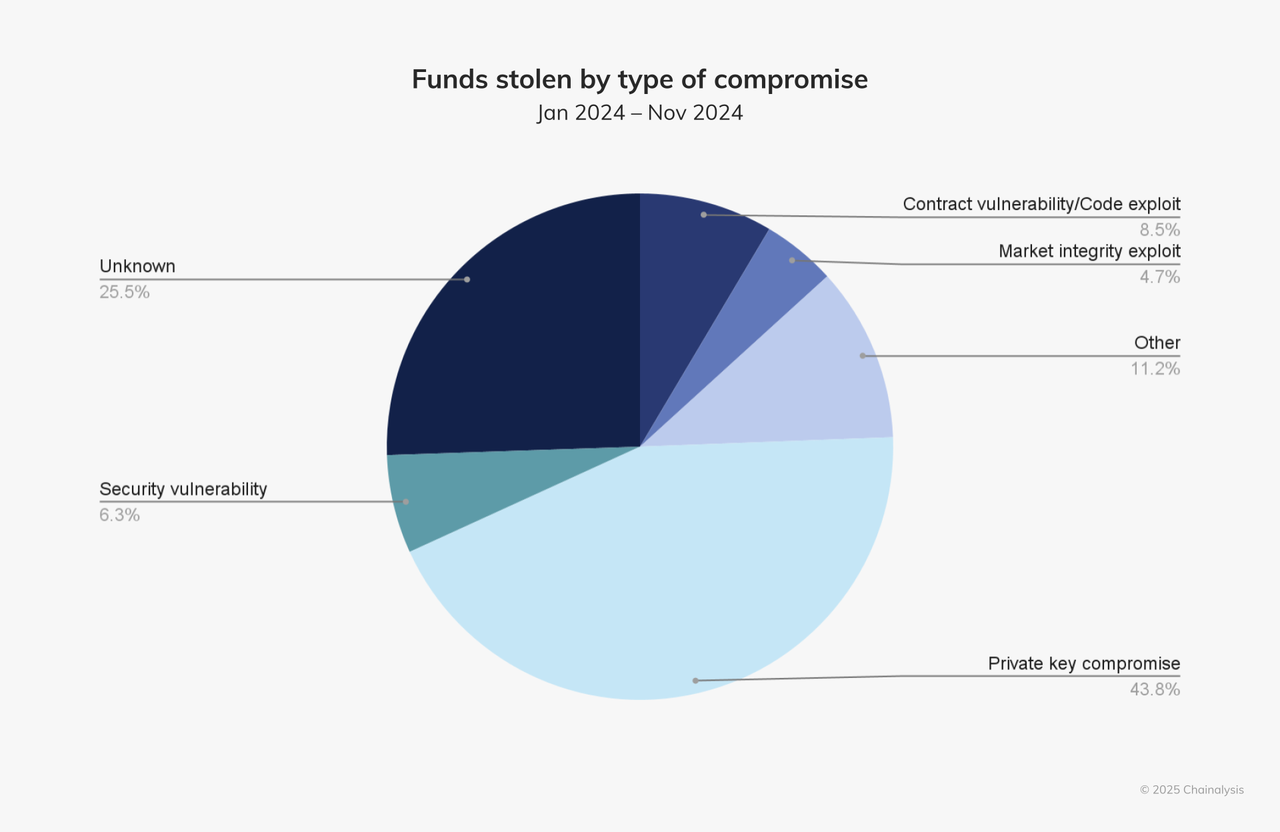
Attack type distribution :
- DeFi projects were attacked the most, accounting for 50.7%.
- CEX suffered the largest loss, totaling $724 million .
- The largest losses were caused by private key leaks, with 35 incidents resulting in losses of $1.306 billion .
- Significant changes in the medium term
- The amount of money stolen from January to July reached $1.58 billion, an increase of 84.4% year-on-year.
- After July, the growth in attack intensity and amount stagnated, which may be related to geopolitical events.
Review of major attacks
1. DMM Bitcoin was stolen
- Date : May 31, 2024
- Cost : $304 million
- Attack method : private key leakage
- Analysis : Attackers targeted vulnerabilities in the infrastructure used by DMM to conduct unauthorized withdrawal transactions
2. PlayDapp Attack
- Date : February 9, 2024
- Cost : $290 million
- Attack method : private key leakage
- Analysis : The hacker made profits by minting PLA tokens multiple times and tried to launder the assets through multiple exchanges.
3. WazirX phishing attack
- Date : July 18, 2024
- Cost : $235 million
- Attack method : Multi-signature phishing attack to induce contract upgrade.
4. Gala Games Privileged Access Control Vulnerability
- Date : May 20, 2024
- Cost : $216 million
- Attack method : Use the privileged addresses obtained by hackers to mint tokens.
5. Chris Larsen Wallet Attack
- Date : January 31, 2024
- Cost : $112 million
- Attack method : private key leakage.
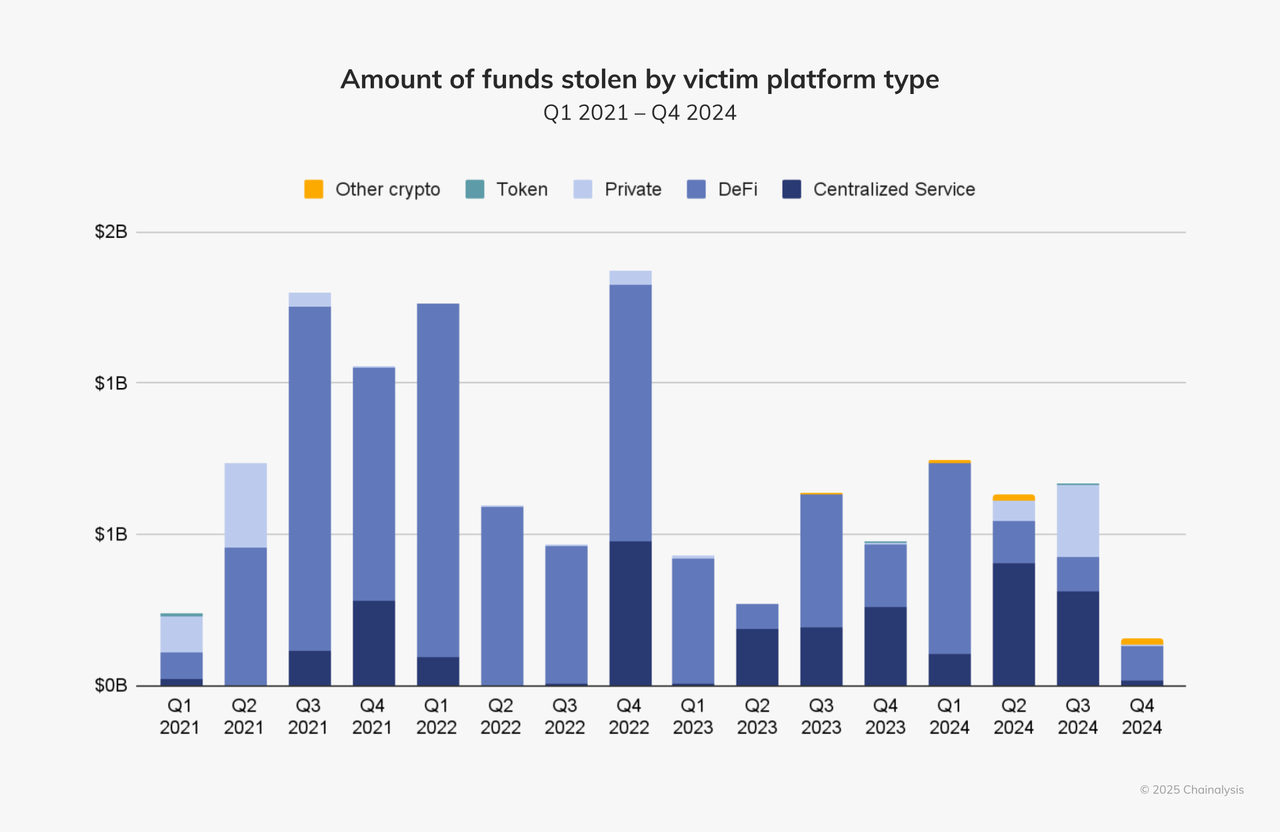
Attack patterns by platform and method
- The changing roles of DeFi and centralized services
- DeFi platforms remained the main target in the first quarter, but after the second quarter, centralized services such as DMM Bitcoin and WazirX became the main targets of hackers.
- Private key theft is the main method, accounting for 43.8% of the total stolen amount.
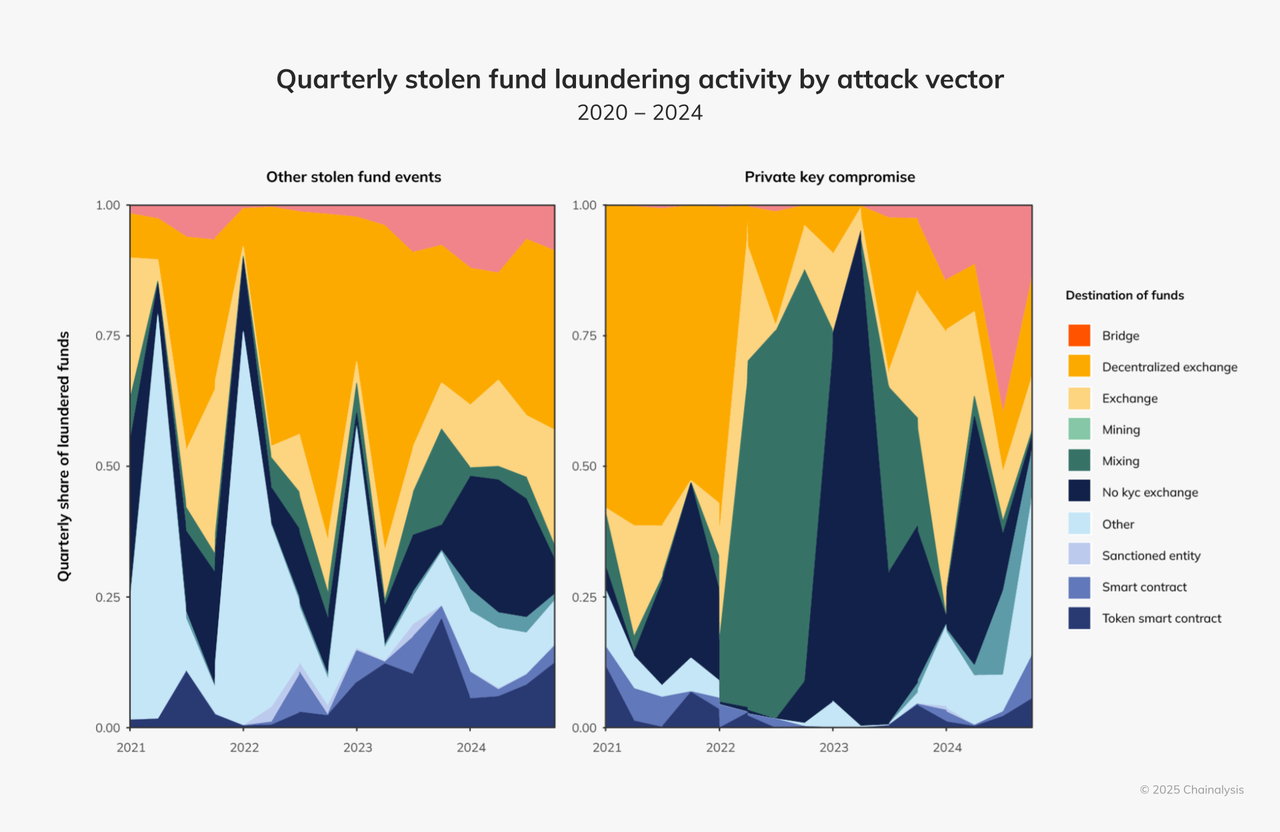
- Funds Laundering ModelHackers tend to disperse funds through cross-chain bridges, DEX, and coin mixers. The use of traditional coin mixing tools has decreased, and the dispersed path of funds has increased the difficulty of investigation.
- Global anti-money laundering measures have been upgraded. The success rate of tracking and freezing stolen funds has increased to 21.13% , demonstrating the effectiveness of anti-money laundering tools and cross-institutional cooperation.
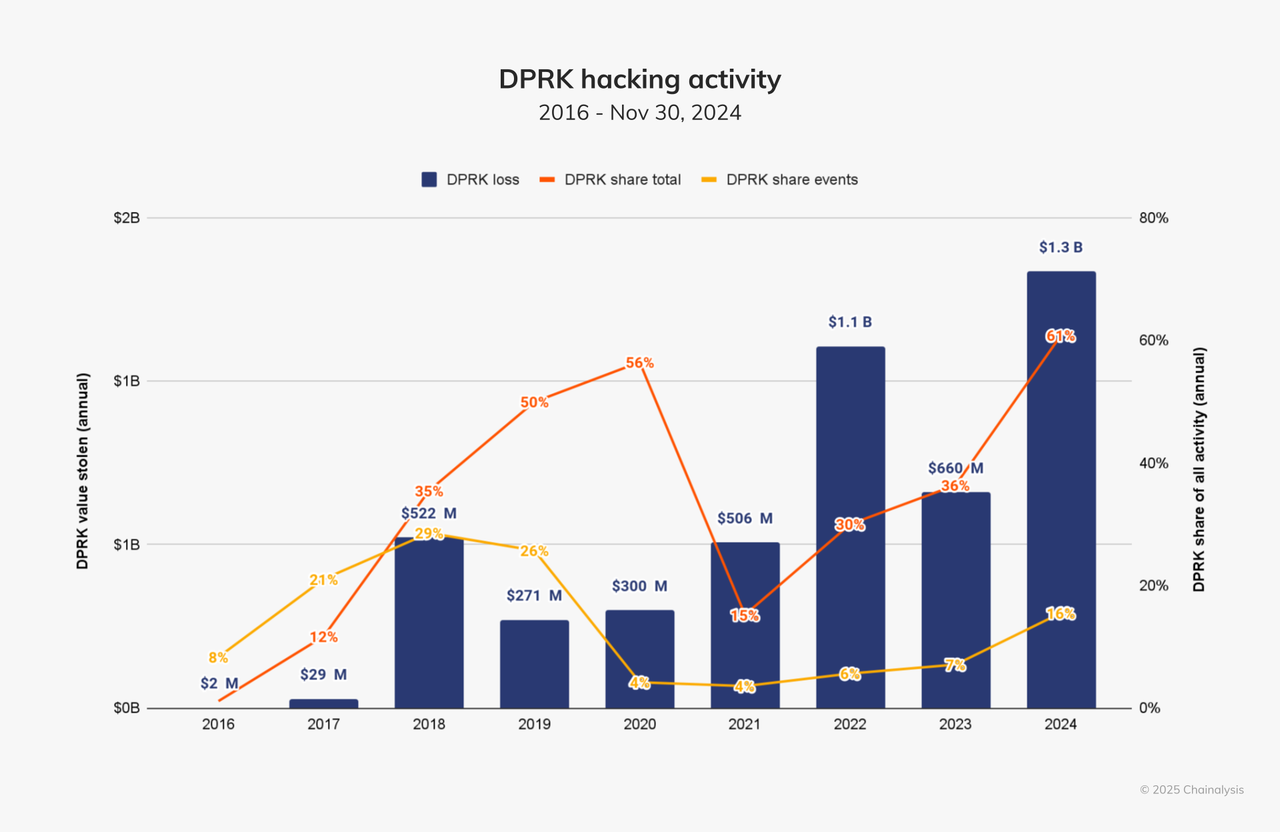
Characteristics of North Korean hacker activity
- Both the amount and number of incidents increased. North Korea-related hackers stole $1.34 billion in 2024, up 102.88% year-on-year, accounting for 61% of the total stolen money for the year. The number of incidents increased from 20 in 2023 to 47, accounting for 20% of the total number of incidents.
- Evolution of attack scale: North Korean hackers frequently carry out large-scale attacks ranging from US$50 million to US$100 million and exceeding US$100 million, and small-scale attacks below US$50 million have also increased.
- Key case: DMM Bitcoin In May 2024, North Korean hackers stole $305 million worth of bitcoins from DMM Bitcoin through a private key management vulnerability. This incident revealed the inadequacy of centralized platform security protection.
The North Korea-Russia alliance and the changing pattern of attack
- Trend changes after the June 2024 summit
- After the summit, the average daily amount of money stolen by North Korean hackers dropped by 53.73%, while the amount stolen by non-North Korean hackers increased by 5%.
- It is speculated that this is related to North Korea's diversion of resources to the Ukrainian conflict, but further evidence is needed.
- Infiltration Strategies of IT Workers North Korea has infiltrated Web3 companies through remote work positions, using sophisticated tactics to steal assets and data, further expanding its reach.
Summary and suggestions
- The industry needs stronger protection measures
- Strengthen private key management and identity authentication.
- Public-private collaboration to build more comprehensive security mechanisms.
- Monitoring North Korea and geopolitical developments
- Focus on tracking the impact that the North Korea-Russia alliance may have on future attack patterns.
- Be vigilant during the holidays and guard against high-risk attacks.
Future Outlook
As the blockchain ecosystem continues to expand, security will continue to face challenges. However, technological innovation and international cooperation are driving the construction of a stronger defense system. By improving tool capabilities, improving the regulatory environment, and raising awareness among practitioners, we have reason to look forward to a safer blockchain future.

