CRVA integrates four cutting-edge cryptographic technologies: zero-knowledge proofs (ZKPs), ring-verifiable random functions (Ring-VRFs), multi-party computation (MPC), and trusted execution environments (TEEs). This builds a truly decentralized verification network, enabling mathematically provably secure blockchain application infrastructure. This innovation not only technically breaks the limitations of traditional verification models but also conceptually redefines the path to decentralization.
Cryptographic Random Verification Agent (CRVA): The Technical Core of DeepSafe
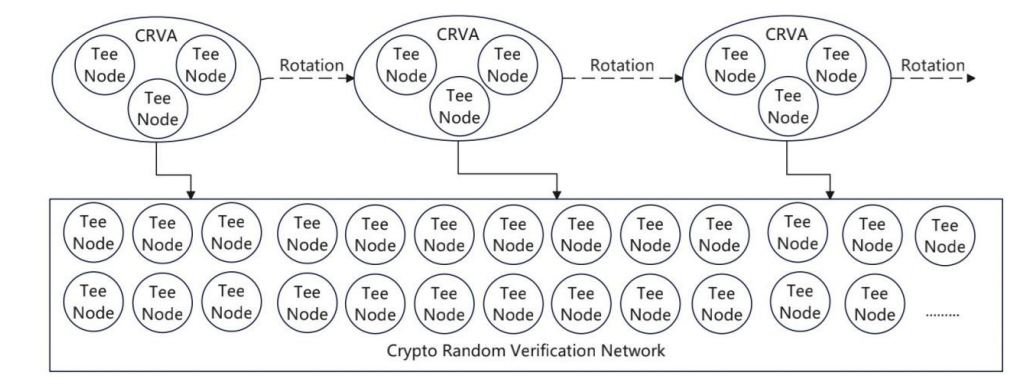
The Crypto Random Verification Agent (CRVA) is the core of DeepSafe's technical architecture. It is essentially a distributed verification committee composed of multiple randomly selected verification nodes. Unlike traditional verification networks that explicitly designate specific validators, nodes in the DeepSafe network are unaware of the selected validators, fundamentally eliminating the possibility of collusion and targeted attacks. The CRVA mechanism solves the long-standing key management dilemma in the blockchain world. Traditionally, verification authority is typically concentrated in a fixed set of multi-signature accounts or nodes, such as the supernodes that manage private keys in traditional CEXs. If these known entities are attacked or collude to commit malicious acts, the security of the entire system will collapse. Through a series of cryptographic innovations, CRVA achieves an "unpredictable, untraceable, and untargetable" verification mechanism, providing mathematically sound assurance for asset security. CRVA operates based on three principles: anonymity of members and verification content, dynamic rotation, and threshold control. The identities of validating nodes in the DeepSafe network are strictly confidential, and the verification committee is regularly randomly reorganized. During the verification process, a threshold multi-signature mechanism ensures that only a certain percentage of nodes (e.g., 9 out of 15 members) must cooperate to complete the verification. Validators in the DeepSafe network are required to stake a significant amount of DeepSafe tokens, and the DeepSafe committee's slashing mechanism for striked nodes increases the cost of attacking validators. CRVA's dynamic rotation and anonymity, combined with the validator node slashing mechanism, theoretically make attacking DeepSafe validators to steal transactions nearly as difficult as attacking the entire network. Current computing power alone is simply not feasible for attacking DeepSafe validators. CRVA's technological innovation stems from a profound rethinking of traditional security models. While most existing solutions focus solely on preventing known validators from acting maliciously, CRVA addresses a more fundamental question: how to ensure that no one, including the validators themselves, knows who the validators are, preventing both internal malicious activity and external hacking, thereby eliminating the possibility of centralization of power. This shift in thinking represents a transition from the "human honesty assumption" to "mathematically proven security."
CRVA's innovation is based on the deep integration of four cutting-edge cryptographic technologies, which together form a mathematically provably secure verification system. Before delving into each technology, let's briefly understand their basic functions and synergies:
In-Depth Analysis of CRVA's Four Core Technologies
Technical Overview and Synergies
CRVA's innovation is based on the deep integration of four cutting-edge cryptographic technologies, which together form a mathematically provably secure verification system. Before diving into each technology, let's briefly review their basic functions and synergies:
-
Ring Verifiable Random Function (Ring-VRF): Provides verifiable randomness and anonymity to external observers, making it impossible to determine which nodes are selected as validators.
-
Zero-Knowledge Proof (ZKP): Enables nodes to prove their eligibility to verify transactions without revealing their identities, protecting node privacy and communication security.
-
Multi-Party Computation (MPC): Implements distributed key generation and threshold signatures, ensuring that no single node possesses the complete key. Furthermore, distributed keys and threshold signatures effectively prevent efficiency issues that could lead to system failures due to single points of failure.
-
Trusted Execution Environment (TEE): provides a hardware-level isolated execution environment, protecting sensitive code and data. Neither node owners nor node maintenance personnel can access or modify the node's internal data.
These four technologies form a tight security loop within CRVA, complementing and reinforcing each other to build a multi-layered security architecture. Each technology addresses a core challenge in decentralized verification, and their systematic combination makes CRVA a trustless, secure verification network.
Ring Verifiable Random Function (Ring-VRF): Combining Randomness and Anonymity
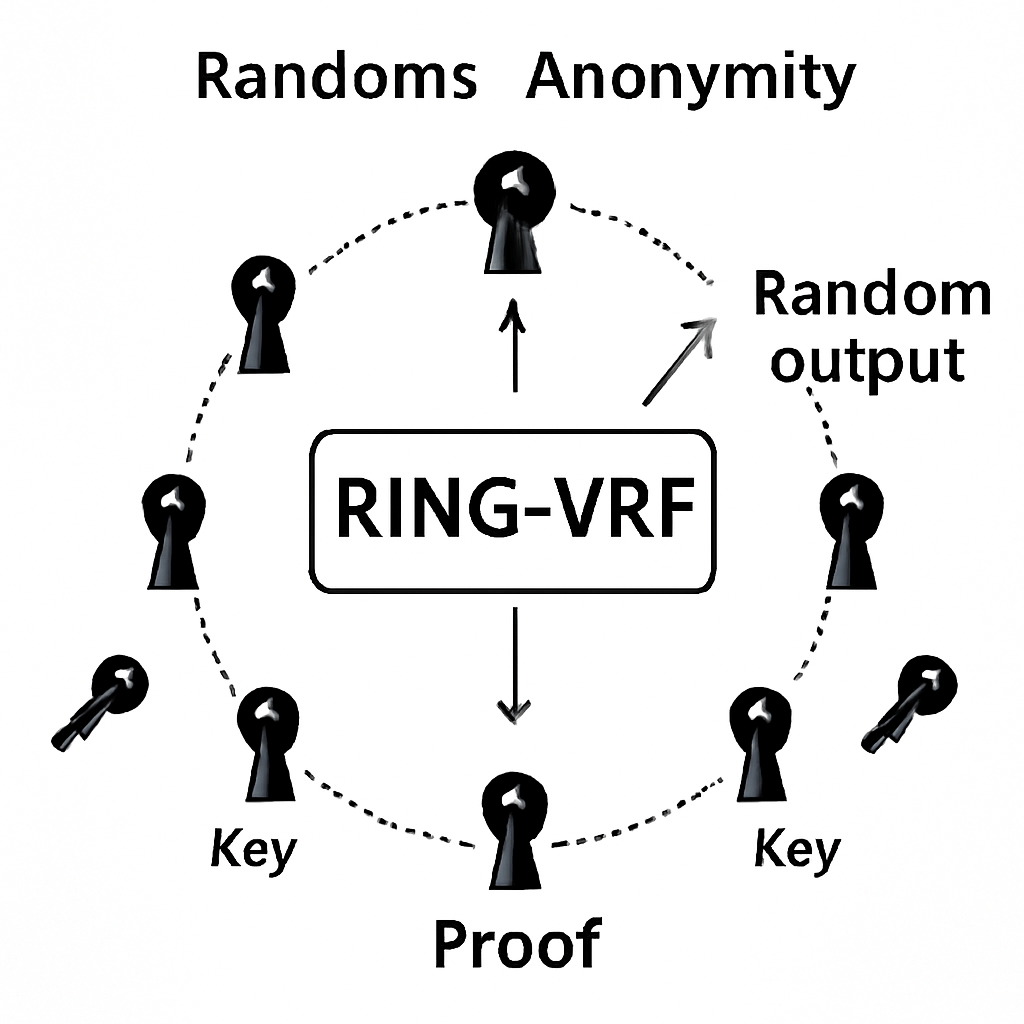
Ring Verifiable Random Function (Ring-VRF) is one of the core innovative technologies in CRVA. It solves the key problem of "how to randomly select validators while preserving the privacy of the selection process." Traditional Verifiable Random Function (VRF) is a cryptographic tool that allows users holding a specific private key to generate publicly verifiable random numbers. However, this process reveals the identity of the generator. Ring signatures are a technology that allows the signer to remain hidden within a group. Ring-VRF combines the strengths of these two technologies, achieving both verifiable randomness and anonymity from external observers.
Ring-VRF innovatively places the public keys of multiple VRF instances into a "ring." When a random number is generated, the system can confirm that it was indeed generated by a member of the ring, but cannot identify the specific one. This way, even though the random number generation process is verifiable, the generator's identity remains anonymous to external observers. When a verification task arrives, each node in the network (which has its own long-term key pair) generates a temporary identity and places it into a "ring." The system uses this ring for random selection, but thanks to the protection of the ring signature mechanism, external observers cannot determine the specific nodes selected.
Ring-VRF provides two layers of protection for CRVA. Ring-VRF ensures the randomness and verifiability of the node selection process and protects the anonymity of the selected nodes, making it impossible for external observers to determine which nodes participated in the verification. This design significantly increases the difficulty of attacks against validators. Within the CRVA mechanism, through deep integration with Ring-VRF, ZKP, MPC, and TEE technologies, a complex verification participation mechanism is constructed, significantly reducing the possibility of inter-node collusion and targeted attacks.
Zero-Knowledge Proof (ZKP): Mathematical Guarantees for Hidden Identity
Zero-Knowledge Proof (ZKP) is a cryptographic technique that allows one party to prove a fact to another without revealing any information other than the fact that the fact is true. In CRVA, ZKP is responsible for protecting the privacy of node identities and the verification process. In traditional node communication, the prover is typically required to present the entire proof to the verifier. In a zero-knowledge proof, the prover can convince the verifier that a statement is true without revealing any specific information supporting the statement.
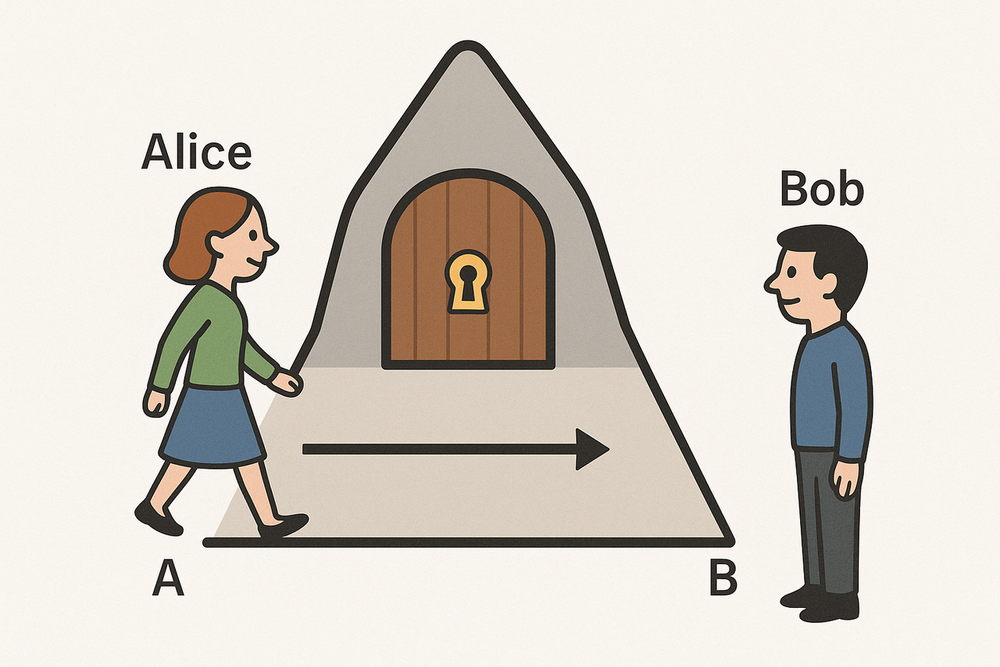
For example, a cave has entrance A and exit B, with a password-protected door in the center. Alice enters entrance A, uses the password to open the door, and exits through the cave through exit B. Bob, observing the entire process from outside and knowing there are no other possible exits, believes Alice has the password to open the door, but Alice doesn't need to tell Bob the password.
CRVA uses ZKP to implement two key functions. Each validating node in the network possesses a long-term identity (i.e., a permanent key pair). However, directly using these identities poses a security risk by exposing the node's identity. Using ZKP, nodes can generate temporary identities and prove their legitimacy without revealing their specific identity. When participating in a validation committee, nodes must communicate and collaborate with each other. ZKP ensures that these communications do not reveal a node's long-term identity, allowing nodes to prove their eligibility without revealing their true identity. ZKP technology ensures that even by observing network activity over a long period of time, attackers cannot determine which nodes participated in the validation of a specific transaction, thus preventing targeted attacks and long-term analysis. This is a key foundation for CRVA's long-term security.
Multi-Party Computation (MPC): Distributed Key Management and Threshold Signatures
Multi-Party Computation (MPC) technology addresses another key issue in CRVA: securely managing the keys required for validation, ensuring that no single node can control the entire validation process. MPC allows multiple parties to jointly compute a function while keeping their inputs private. Simply put, participants can collaborate on a computation, knowing only their own portion of the inputs and outputs and unaware of others' secret information. This is like multiple people working together to complete a puzzle, each responsible for their own piece, yet ultimately completing the puzzle. In CRVA, when a group of nodes is elected as a validation committee, they require a shared key to sign the validation results. Using the MPC protocol, these nodes collectively generate a distributed key, each holding only a fragment of the key, and the full key never resides on any single node. CRVA also sets a threshold (e.g., 9 out of 15 nodes) that must be met to generate a valid signature. This ensures that the system remains operational even if some nodes are offline or under attack, ensuring overall system efficiency. MPC technology enables validation nodes to complete validation securely and efficiently even under unstable network conditions. This optimization accounts for the complexity and uncertainty of blockchain networks, ensuring reliable verification in a variety of network environments.
To further enhance security, CRVA fully implements the MPC technology system, including distributed key generation (DKG), a threshold signature scheme (TSS), and a key handover protocol. The system achieves complete key shard updates by regularly rotating the verification committee members.
This design creates the critical "time isolation" security feature. The committee of CRVA nodes rotates periodically (initially every 20 minutes), expiring old key shards and generating new ones for the new members. This means that even if an attacker successfully compromises some nodes and obtains key shards during the first period, these shards will be completely invalid after the next rotation period.
Assuming the threshold requirement is 9 out of 15 nodes, an attacker cannot obtain 9 valid shards by compromising 3 nodes today, 3 nodes tomorrow, and 3 nodes the day after tomorrow, because the shards obtained in the previous two days will have already expired. To pose a threat, an attacker must simultaneously control at least nine nodes within the same rotation cycle, significantly increasing the difficulty of an attack and effectively protecting CRVA from long-term, persistent attacks.
Trusted Execution Environment (TEE): Physical Security and Code Integrity Assurance
The Trusted Execution Environment (TEE) is another line of defense within the CRVA security framework, providing hardware-level security for code execution and data processing. A TEE is a secure area within modern processors, isolated from the main operating system, providing an independent, secure execution environment. Code and data running within the TEE are protected at the hardware level, ensuring that even if the operating system is compromised, the contents within the TEE remain secure. This is like creating a physically isolated "safe" within the computer, where only specifically authenticated programs can run.
In the CRVA architecture, all critical authentication processes run within the TEE, ensuring that the authentication logic cannot be tampered with. Each node's key shards are stored in the TEE, preventing even node operators from accessing or extracting this sensitive data. The aforementioned technical processes, such as Ring-VRF, ZKP, and MPC, are all executed within the TEE, preventing the leakage or manipulation of intermediate results.
CRVA offers multiple improvements over traditional TEE technology. CRVA doesn't rely on a single TEE implementation (such as Intel SGX), but rather supports multiple TEE technologies, reducing reliance on specific hardware vendors. Furthermore, CRVA optimizes the security of data exchange within and outside the TEE, preventing data from being intercepted or tampered with during transmission. The TEE provides "physical-level" security for CRVA, forming a comprehensive, integrated hardware and software protection framework alongside the other three cryptographic technologies (Ring-VRF, ZKP, and MPC). Cryptography provides mathematical security, while the TEE physically protects code and data from being stolen or tampered with. This multi-layered protection ensures CRVA's exceptional security.
CRVA Workflow: The Art of Technological Fusion
After understanding the four core technologies of CRVA, the following describes how CRVA's workflow demonstrates their synergy, forming a seamlessly integrated security verification system. Taking a typical cross-chain verification scenario as an example, CRVA's operation can be divided into five key phases:
1. Initialization and Node Joining
During the network's initialization phase, nodes register and join the DeepSafe network through a standard process. Each node generates a long-term identity key pair and configures the TEE environment and necessary network parameters. This process uses zero-knowledge proof technology to verify node qualifications, ensuring that only legitimate nodes can join the network.
Notably, this phase does not involve the selection of the validation committee. All nodes exist solely as network participants, and no node knows whether it will be selected as a validator. This design prevents targeted attacks against validating nodes from the source.
2. Task Triggering and Validator Selection
When a verification request (such as a cross-chain transaction) occurs, the system initiates the verification committee selection process. All active nodes generate temporary identities and submit zero-knowledge proofs to prove their legitimacy in the network without revealing their long-term identities. These temporary identities form a "ring." The system uses the Ring-VRF algorithm to randomly select a specific number of nodes (e.g., 15) from this ring to form the verification committee. Protected by zero-knowledge proofs and ring signatures, no one (including the selected nodes themselves) knows which nodes have been selected.
3. Key Generation and Distribution
Selected nodes collaborate to generate a distributed private key through a complex multi-party computation protocol. Each node holds only a fragment of the private key, and the full private key is never stored in any single location. The entire process is performed within a TEE environment, ensuring that even node operators cannot access key information. The system sets a threshold parameter (e.g., 9 out of 15), requiring the cooperation of at least the threshold number of nodes to complete a valid signature. This mechanism ensures the system remains operational even if some nodes are offline or attacked, while also preventing small-scale collusion.
4. Verification Execution and Signature Generation
The verification committee receives verification requests (such as cross-chain messages), and each member independently verifies their validity within the TEE. Once verification is successful, the node participates in the distributed signing process using its private key shards. When a threshold number of nodes submit valid signature shards, the system aggregates these shards through multi-party computation to generate a complete signature. Due to the confidentiality of this process, external observers only see the final signature result and cannot determine the specific nodes involved in the signature.
5. Periodic Rotation and Secure Destruction
To prevent long-term analysis attacks, CRVA implements a periodic rotation mechanism. Even if the current verification committee is performing well, the system periodically initiates a new round of validator selection to reselect nodes to form a new committee. Each newly formed committee generates a key shard and begins a new round of verification. The key shards of the previous committee become invalid. This periodic rotation mechanism significantly enhances the system's resistance to long-term attacks.
The entire process forms a closed-loop security verification system, with each step meticulously designed to ensure the anonymity, randomness, and unpredictability of the verification process. Four core technologies work closely together at every stage to build a mathematically provably secure verification network.
Innovative Breakthroughs in the CRVA Mechanism
Traditional cryptographic schemes face a common challenge when applied to blockchain verification networks. As the number of participating nodes increases, computational complexity and communication overhead increase exponentially, forcing the system to compromise between decentralization and operational efficiency. This is particularly true for ring signatures and multi-party computation in large-scale networks, forcing most existing projects to limit the number of participating nodes, weakening decentralization.
DeepSafe innovatively combines Ring-VRF and MPC technologies to achieve a groundbreaking "large network, small committee" architecture. The entire DeepSafe network consists of 400 nodes, but only a small number of nodes (e.g., 10) are randomly selected to form the committee for each verification. This small size of the dynamic committee significantly reduces network computation and communication costs. CRVA regularly rotates committee members through Ring-VRF and MPC, ensuring efficient verification while maintaining overall decentralized security across the DeepSafe network.
This design elegantly addresses the limitations of traditional solutions. Compared to multi-sig schemes with fixed validators, CRVA provides higher security; compared to fully decentralized but inefficient solutions, CRVA maintains superior performance. Through technological innovation and system design, DeepSafe successfully achieves these two seemingly contradictory goals, striking a balance between efficiency and security.
Secondly, DeepSafe doesn't use ZKP technology for common transaction privacy protection or Layer 2 data compression, but instead pioneers its application to the identity anonymity of the verification network itself. The CRVA system employs a lightweight ZKP scheme focused on protecting the identity of verification nodes, ensuring that nodes can prove their credentials without revealing their true identities. This application circumvents the high computational complexity of traditional ZKP implementations, as the proof structure for identity verification is relatively simple and can be efficiently generated and verified.
Through this innovative application, DeepSafe provides key technical support for verifier anonymity while avoiding the performance bottlenecks of ZKP in more complex application scenarios, opening up a new path for privacy protection in blockchain verification networks.
Conclusion: A New Paradigm for Decentralization
DeepSafe's Cryptographic Random Verification Agent (CRVA) technology represents a new paradigm for blockchain security and decentralization. Through the deep integration of zero-knowledge proofs, ring-verifiable random functions, multi-party computation, and a trusted execution environment, CRVA achieves the ideal state of "validator anonymity, random selection, and process confidentiality," fundamentally addressing the centralization risks inherent in traditional verification models. CRVA's innovation lies not only in its technical implementation but also in a shift in mindset—from "how to prevent known validators from committing malicious acts" to "how to ensure, from the source, that no one knows who the validator is." This shift in thinking enables CRVA to provide mathematically provable security guarantees, rather than relying on artificial assumptions of honesty. With the deep integration of blockchain and AI technologies, the importance of trusted data verification is becoming increasingly prominent. CRVA, serving as a bridge connecting the on-chain and off-chain worlds, provides security for cross-chain assets. It also provides reliable verification of AI agent input and output information, building a truly decentralized, trusted data infrastructure. In the future, with the further development of cryptographic technology and hardware security solutions, CRVA will continue to optimize and evolve, providing more secure and efficient verification services for the blockchain ecosystem and promoting the expansion of decentralized technology to a wider range of application scenarios.

