
In the previous article "Can projects go overseas to avoid Chinese law? Compliance misunderstandings that Web3 entrepreneurs cannot ignore", Lawyer Shao mentioned:
A compliance misunderstanding that Web3 entrepreneurs and practitioners tend to overlook is that as long as the project is registered overseas and the server is deployed overseas, "natural compliance" can be achieved.
But in reality, the core of compliance lies in the business model, capital structure and operation substance of the project itself, rather than the superficial overseas structure. In other words, overseas registration can be a part of compliance, but it cannot be a shield to cover up high-risk business practices. In particular, for teams that still reside in China and provide services to Chinese users, they should pay special attention to the legal boundaries and criminal compliance risks of the project.
This article will further analyze: As a developer, how can you quickly determine whether a Web3 project is a "criminal red line project"? We will take the four types of Web3 illegal risk models that are common in practice as examples to help developers establish basic recognition capabilities from the perspectives of project structure, system functions, token circulation, etc. As long as you can identify and avoid these high-frequency project types in the early stages, you can hopefully stay away from most criminal legal risks.
lAuthor: Lawyer Shao Shiwei
First of all, it needs to be stated that this article is aimed at technical practitioners who hope to develop in the Web3 industry in the long term, especially developers who attach importance to project compliance construction and have a certain awareness of legal risks. Our analysis objects also focus on projects with basic compliance awareness and certain business planning capabilities.
As for fake projects set up for the explicit purpose of illegal fundraising, cryptocurrency fraud, money laundering and arbitrage, they are not within the scope of analysis in this article.
1
How do developers build a “high-risk project identification radar”?
In this section, we will use typical Web3 criminal cases to analyze four types of high-frequency crimes and typical cases related to developers in current judicial practice .
Based on the practical experience of Lawyer Shao’s team in handling Web3 criminal cases in recent years, we have summarized them into four categories: “most dangerous, most hidden, most obvious and currently hottest”.
The purpose of this classification is to enable developers to establish a basic understanding of these crimes and the judicial status quo behind them. Only by knowing what the "red line" is can we talk about how to identify it, how to avoid it, and how to participate in the project safely.
1. The most dangerous crime: [Opening a casino]
In the Web3 field, gambling-related projects are the most likely type of projects for technical developers to "step on minefields", especially in GameFi or chain game systems.
Common gambling-related project models that are held accountable include:
• Gambling DApp (decentralized gambling application);
• Online casino platforms that use USDT or other virtual currencies for betting;
• On-chain games with random gameplay logic such as raffles, unboxing, blind boxes, etc.
Since the construction of a closed gambling loop often relies on smart contract logic and wallet interaction, developers play a key role in technical implementation. Therefore, even non-platform operators may be held accountable as accomplices for system development activities.
As a common business model in Web3 projects, blockchain game GameFi is regarded as a high-risk criminal cluster due to its natural gambling attributes of "recharge-random gameplay-withdrawal".
Case reference:
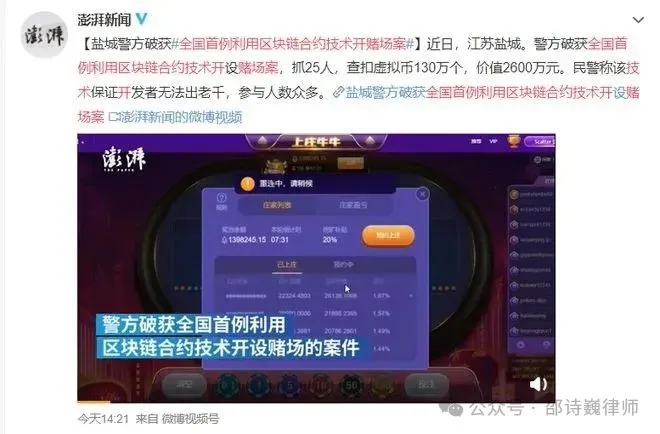
For example, the "BigGame case" is the first criminal case in China where the crime of opening a casino was triggered by blockchain contract logic. The development team involved in the case is located in China. The platform it built allows users to install a EOS wallet, convert RMB into virtual currency, and then participate in on-chain betting, thus realizing a complete "digital wallet-betting-settlement" gambling closed loop. This case directly shows that as long as the technical developers are deeply involved in the construction of the system, even if they do not directly operate the platform, they may constitute a technical accomplice in opening a casino.
summary:
In practice, we have seen a large number of technical developers passively involved in gambling-related projects because they failed to identify the "gambling logic" - especially those who are deep participants in modules such as wallet systems, reward mechanisms, and contract interfaces, who are more likely to become the focus of police investigations.
In the following chapters, we will focus on another type of high-risk projects that are often "disguised as sheep's clothing": those project structures that are presented in the form of "new customer rewards", "rebate fission" and "community incentives", but may actually constitute the crime of organizing and leading pyramid schemes.
2. The most hidden crime: [Organizing and leading pyramid selling activities]
The "hiddenness" of this crime is that it often appears in the guise of "attracting new users", "community incentives" and "node rebates". For Web3 projects, rebates, fission and invitation rewards have almost become the default configuration, so it is easy for technical developers and operators to have cognitive misunderstandings: what kind of incentives are normal business behaviors, and what kind of models may constitute pyramid schemes?
Common MLM project models include:
Air coin or platform coin projects, through "paying money to obtain investment qualifications";
Multi-level reward structure, rebate for recruiting people, and developing downline;
Node Program/Ambassador Mechanism: Relying on “headcount” to gain revenue, not on the product or service itself.
Case reference:
For example, the "3M Platform MLM Case" heard by the Xichou County Court in Yunnan: the project builder created the virtual currency investment platform "3M", claiming that investing in its platform tokens could generate high returns, and designed two income structures - static income (i.e. fixed interest rate) and dynamic income (i.e. commission for developing downlines). Upon investigation, it was found that the platform had a membership structure of more than three levels and a large number of participants, and was eventually identified as organizing and leading MLM activities.
In many MLM cases handled by our team, many developers were responsible for building rebate systems, writing hierarchical databases, and designing a complete set of revenue logic, but they lacked the ability to judge whether the model constituted a MLM. Once the overall structure of the platform is identified as a MLM by the judicial authorities, programmers who are at the core of the project and play a key technical support role in the operation of the model are likely to be identified as co-conspirators.
summary:
"Rebates for recruiting people" cannot be completely equated with pyramid schemes, but once the incentive structure is based on "payment of entry + commissions at each level + pyramid-like levels", even if technical personnel only participate in the development of the back-end system, they may be included in the criminal accountability chain due to their "indispensability".
In the next section, we will move on to a type of crime with a clearer characterization and relatively clearer judicial standards - the crime of illegally absorbing public deposits/the crime of fund-raising fraud .

3. The most clear-cut crime - [crimes related to illegal fund-raising] (illegally absorbing public deposits/fund-raising fraud)
There are indeed certain legal gaps in the Web3 industry, but my country's regulatory attitude towards the act of "issuing coins for financing" has long been clear. As early as the "94 Announcement" in 2017, it was pointed out that ICO (initial coin offering) is an illegal financial activity and is suspected of illegal fundraising and other crimes. At the same time, the Supreme People's Court's Interpretation on Several Issues Concerning the Specific Application of Laws in the Trial of Criminal Cases of Illegal Fundraising (Revised in 2022) also stipulates that those who illegally absorb funds through virtual currency transactions and other means should be convicted and punished for the crime of illegally absorbing public deposits.
If technical developers are deeply involved in modules such as the token issuance system, mining machine rebate logic, and point redemption structure, even if they do not directly raise funds from the outside, they may be held legally responsible for building a closed-loop funding system and assisting in illegal fund-raising.
In Web3 projects, common patterns involving illegal fundraising include:
Issuing tokens for financing without financial regulatory approval;
Promises of high returns, static dividends, and principal-guaranteed repurchases;
Fake financial management platforms and mining machine investment platforms;
Set up a fund pool and redeem tokens or points within the platform.
The key points for identifying illegal fundraising patterns in Web3 projects mainly include the following high-frequency behaviors:
• Conducting ICO financing through “platform coins” or “governance coins” without the permission of financial regulatory authorities;
• The platform promises “capital preservation and high interest”, “daily static dividends”, “token buybacks” and other inducements to attract funds;
• Fabricating fund pool products such as “mining machine investment” and “on-chain financial management” to redeem user benefits through a closed-loop fund system;
• Establish a token exchange points system within the platform to convert user assets into cashable “income certificates”.
Case reference:
In the "AIP Platform Case", the technical team built a complete token trading and points release system, the core structure of which includes "mining machine revenue release + platform points exchange + AIP token external transaction". The project actually built a closed-loop fund and raised funds from the public. In the end, the court convicted and punished the person in charge of project development for the crime of illegally absorbing public deposits.
This case warns developers: If the system you are involved in has the three elements of "coin issuance financing + points redemption + withdrawal path", even if you do not participate in marketing and promotion, you may still be held criminally liable for the development of key modules.
summary:
Coin issuance projects are the most likely criminal high-risk areas for current technology developers to step into by mistake. Once the module you develop involves key structures such as token generation logic, fund deposit path, points exchange closed loop, and profit distribution mechanism, you must immediately activate the legal risk identification mechanism to determine whether the project is suspected of illegal fundraising or constitutes illegal fund pool behavior.
Next, we will analyze the crime that has been cracked down on most severely in recent years in practice - illegal business operation .
4. The most popular crime at present: [Illegal business operation]
According to Lawyer Shao’s experience in handling foreign exchange criminal cases, in recent years, judicial authorities have been continuously increasing their efforts to crack down on crimes in the foreign exchange field, and Web3 projects, or "cryptocurrency cases", are only one of the sub-sectors that are being focused on.
This is because virtual currency naturally has the attributes of "strong cross-border liquidity, high anonymity, and circumvention of supervision", and has become the main tool for illegal exchange between RMB and foreign currencies. If developers are responsible for building core components of the system such as currency matching systems, OTC trading modules, legal currency deposit channels or withdrawal paths, there is a high legal risk.
Common high-risk behaviors include:
Provide payment settlement, OTC services, token redemption and other functions;
Operating a platform with RMB legal currency trading entry without permission;
Provide matching intermediary services for virtual currency and foreign currency trading.
Case reference:
For example, in a typical case jointly released by the Supreme People's Procuratorate and the State Administration of Foreign Exchange in 2023, Guo Mouzhao was sentenced to five years in prison for illegal business operation by the Baoshan District Court of Shanghai for setting up a virtual currency matching and exchange platform.
In addition, our team is currently representing a case of "PayFi project suspected of illegal operation". The platform was investigated by the public security organs of a southern province and city on suspicion of illegal operation because it used virtual currency as a medium to conduct RMB and foreign currency arbitrage.
summary:
All aspects of cross-border exchange, over-the-counter matching transactions, and fund deposits and withdrawals involving virtual currency platforms are "key gray areas" that are currently under high pressure from regulators. If the system a technology developer is responsible for is used for exchange matching or fund channel construction, there will be legal risks involved in this crime.
In this article, we systematically sorted out the most common and high-incidence business models of criminal legal risks in four types of Web3 projects, and combined with typical cases to help developers establish basic identification capabilities of "criminal law-level red lines."
Behind these charges are no longer abstract legal provisions, but system logic and functional modules that are actually visible and easily overlooked in developers' daily work.
However, simply knowing where the red line is is far from enough.
How can you quickly make a preliminary judgment when facing a new project? How can you evaluate whether you will be included in the criminal liability chain based on your own role? What lawyers' practical experience and compliance suggestions can help developers master and plan ahead?
We will expand on these contents in detail in the next article:
How to judge whether a project is a failure from a developer's perspective;
Specific judgment dimensions and practical references for four typical high-risk models;
How should developers clearly define the boundaries of their responsibilities and avoid being blamed?
How to identify risk signals, troubleshoot hidden dangers, and stop losses in a timely manner at the beginning of a project?
This article is an original article by lawyer Shao Shiwei. It only represents the author's personal views and does not constitute legal consultation or legal opinion on specific matters. For article reprint, legal consultation, and peer communication, please add: sswls66.

