1. Why can’t Ledger protect against real dangers?
Most people only focus on how to prevent cyber attacks:
✅ Anti-phishing,
✅ Prevent private key leakage,
✅ Anti-hacking...
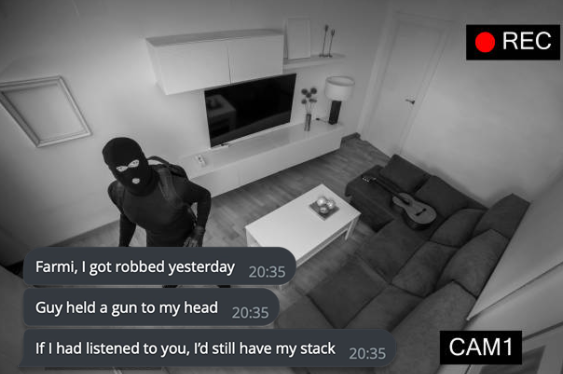
But we forget that in the real world, one person and a gun can allow you to open any wallet.
Data shows:
📈 Home invasions against cryptocurrency users to grow by more than 30% in 2024
Many people think “this won’t happen to me”—
But if you hold more than five figures in USD, you are a target.

2. Decoy Wallet: The first layer of protection for “escape”
No one can stay calm under a gun.
So what you need is to arrange a **“wallet that can be handed over”** in advance.
✅ Practical steps:
Create a new Ledger and generate a new mnemonic
Deposit $1,000 to $3,000 worth of crypto assets
Add some confusion:
❍ Buy a meme coin
❍ Buy a low-priced NFT
❍ Send a few junk transactions
👁 An "empty wallet" is the most suspicious, while a "messy but full wallet" looks normal
3. Ledger hidden wallet function: a true “second identity”
Mainstream wallets such as Ledger provide the **Hidden Wallet** function:
Add a set of "additional passwords (passphrase)" to enter a hidden wallet
Completely independent from the main wallet
Without the password, you will never be able to see the real assets
Just keep a small amount of coins in the main wallet. When forced to open it, give out this "bait wallet". Your real large assets will be safe.

IV. Mnemonic storage strategy: multinational + metallization + multiple dispersion
Once you have high net worth assets, mnemonic storage is more important than the wallet itself.
🛡️ Recommended approach:
Generate mnemonics on a completely offline device
Use metal plate to carve, fireproof and waterproof
Divided into three parts, distributed in different countries or cities
Example layout:
🇨🇭 Words 1 to 8: Swiss bank safe
🇯🇵 Words 9-16: Tokyo Warehouse + Physical Map Guide
🏔 Words 17-24: Hidden under a GPS coordinate in a remote mountain area
Even if someone gets a copy, they cannot recover the complete private key
5. Home safety facilities + behavioral safety strategies
Hardware wallets ≠ security fortresses. You need to build a physical and psychological "double line of defense":
✅ Physical layer:
Install silent alarms, infrared sensors, and cloud surveillance cameras
Do not store mnemonics at home
Establish emergency contacts or a “safety code” mechanism
✅ Behavioral layer:
Stop showing off assets, airdrops, and transaction history on X (Twitter)
Log in to all DApps without main wallet
Change wallets frequently, use VPN, and hardware-isolated signatures

✅ Summary: Staying alive is the most important alpha
We have been working hard on the blockchain for months or even years, and what we have accumulated is not just digital assets.
It is also a freedom and control over the future.
But remember one thing:
Ledger is hacker proof, but not gun proof.
Only "bait + hiding + dispersion + quietness" can truly protect your assets and life.
If you have a crypto asset worth protecting,
Please start building your own "survival system" immediately.

