Background
On June 25, 2025, we monitored an attack on Ethereum against SiloFinance :
https://etherscan.io/address/0xcbee4617abf667830fe3ee7dc8d6f46380829df9
The attack caused a total loss of 54.6k USD .
Attack and incident analysis
First, the attacker called the openLeveragePosition of the contract, which is a function used to open a leveraged position. It uses the flash loan mechanism to implement leveraged trading. Then, in the onFlashLoan callback, _openLeverage is executed to complete operations such as converting the flash loan funds into collateral through _fillQuote.
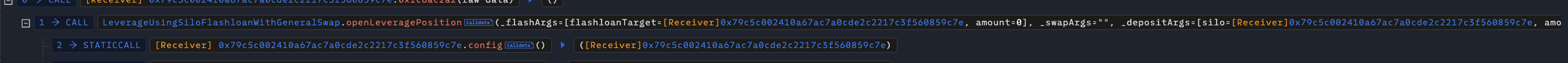
We can see the relevant code:
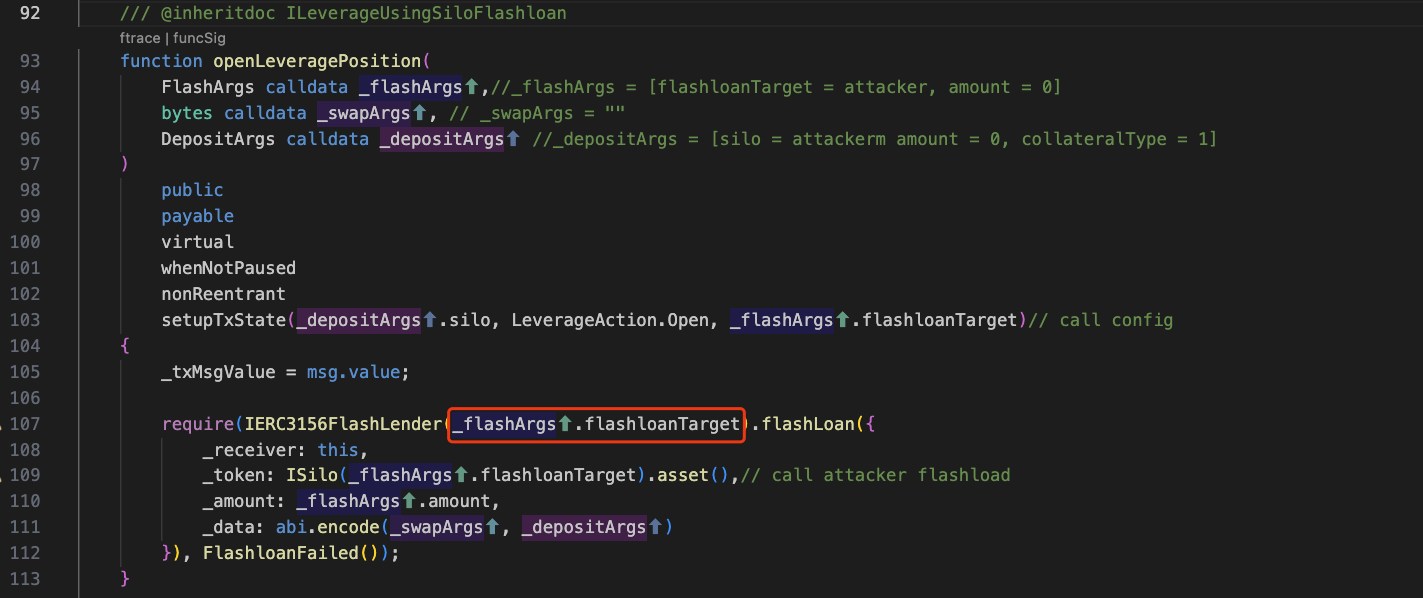
Among them, _flashArgs.flashloadTarget is the attack contract set by the attacker, so this function calls the flashloan of the attack contract.
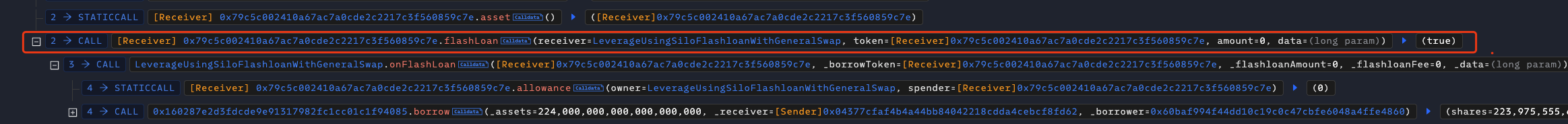
Then, the attack contract calls onFlashLoan, and we can see the relevant code as follows:
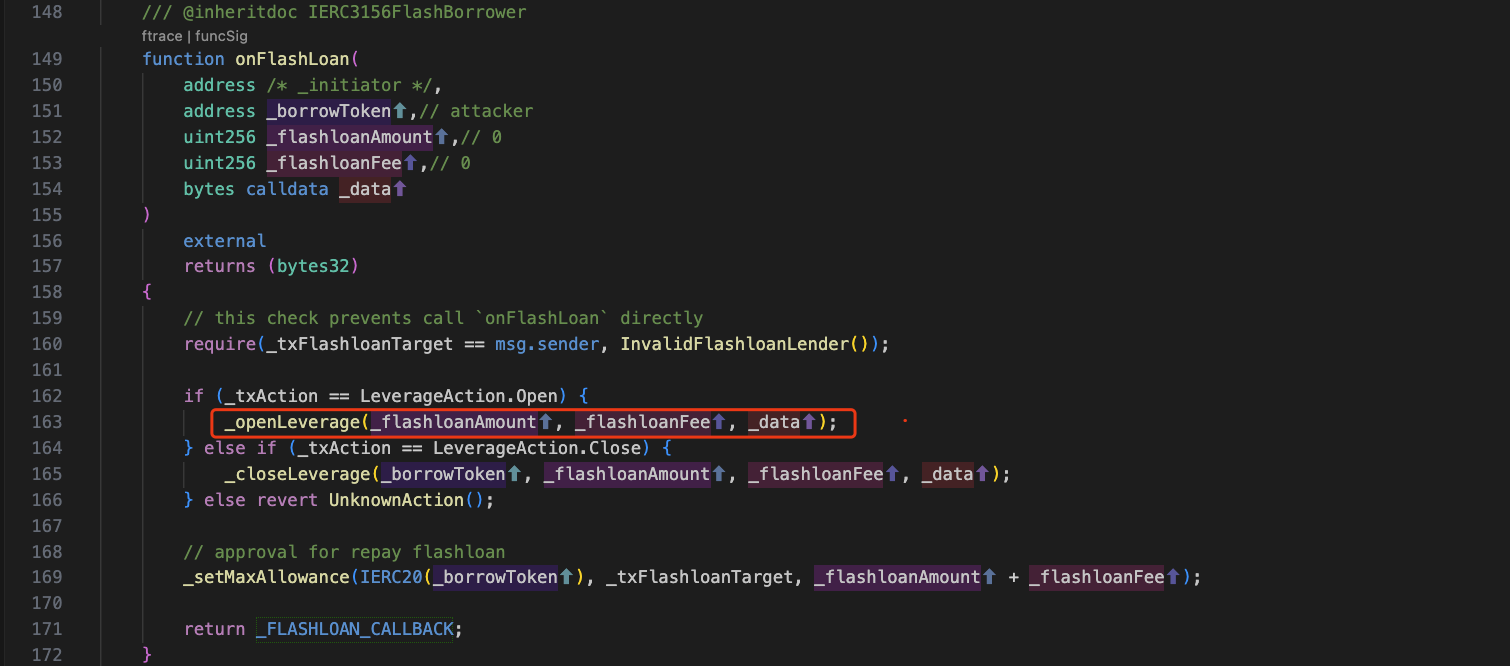
Since _txAction has been set to LeverageAction.Open in the function openLeveragePosition, _openLerverage will be called next.
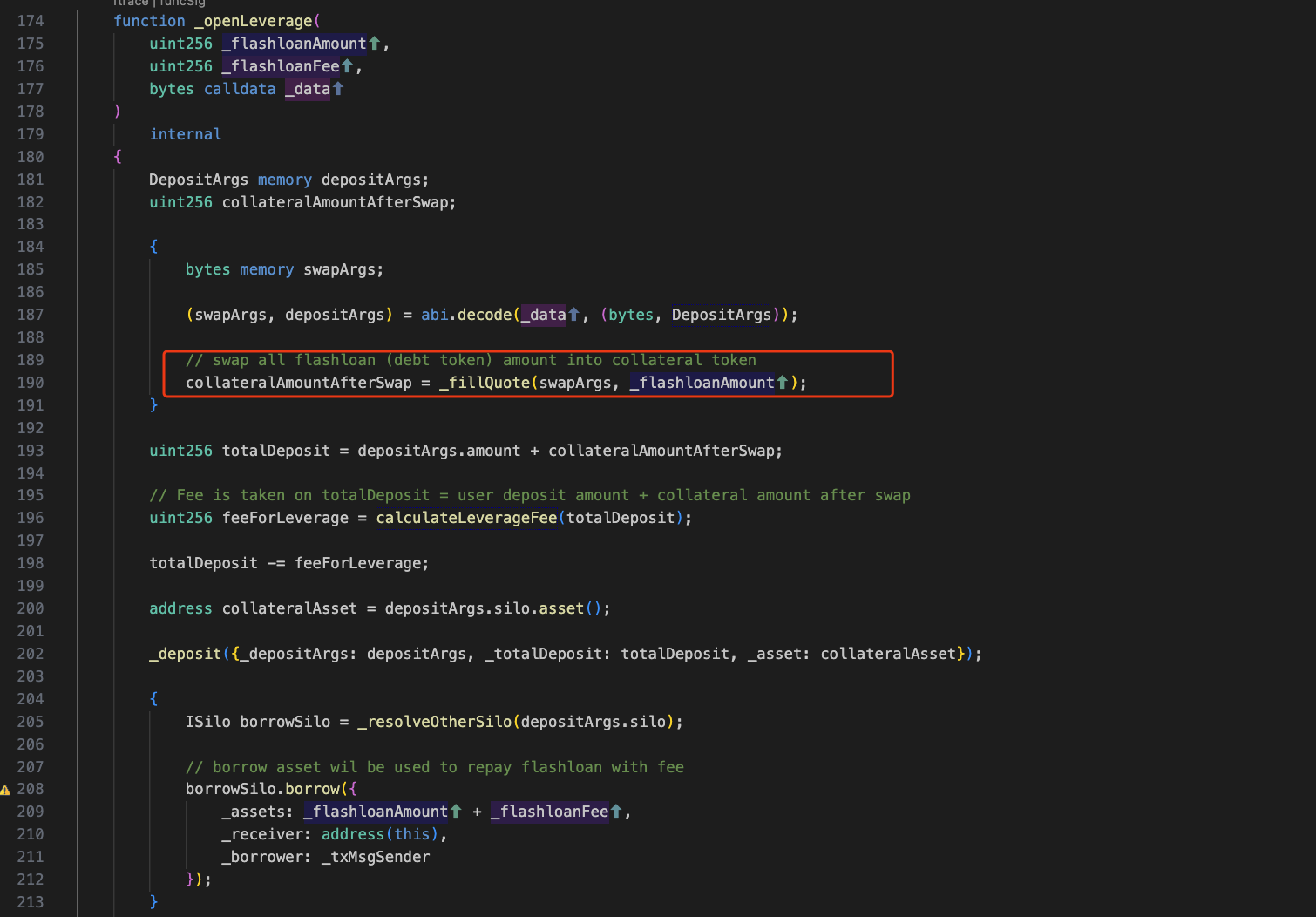
Then _fillQuote is called. The function of this function is to convert debt tokens into collateral tokens. This is where the problem lies. Let's take a look at the implementation of _fillQuote:
struct SwapArgs {
address exchangeProxy; //0x160287e2d3fdcde9e91317982fc1cc01c1f94085
address sellToken; //0x79c5c002410a67ac7a0cde2c2217c3f560859c7e
address buyToken; //0x79c5c002410a67ac7a0cde2c2217c3f560859c7e
address allowanceTarget;//0x79c5c002410a67ac7a0cde2c2217c3f560859c7e
bytes swapCallData; //0xd516418400000000000000000000000000000000000000000000000c249fdd327780000000000000000000000000000004377cfaf4b4a44bb84042218cdda4cebcf8fd6200000000000000000000000060baf994f44dd10c19c0c47cbfe6048a4ffe4860}
We decode the input data, which is swapCallData, and get:
0xd5164184 // borrow(uint256,address,address)
0x00000000000000000000000c249fdd3277800000 //uint256 _assets
0x04377cfaf4b4a44bb84042218cdda4cebcf8fd62 //address _recviver
0x60baf994f44dd10c19c0c47cbfe6048a4ffe4860 //address _borrower
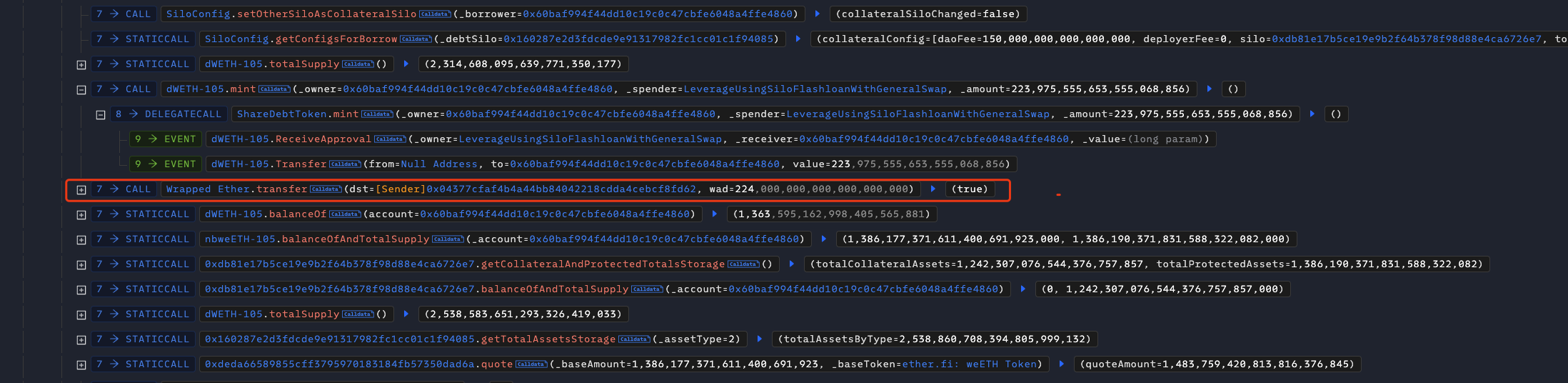
This means that the attacker called the borrow function. Subsequently, the attacker obtained 224 WETH through borrow to complete the attack.
Summarize
The cause of this vulnerability is that the flashloan callback function of the Silo contract did not verify the incoming data, causing the attacker to pass in malicious data and eventually complete the attack on Silo. It is recommended that the project party conduct multi-party verification when designing the economic model and code operation logic, and try to select multiple audit companies for cross-audit when auditing the contract before it goes online.

